Roles Manager - Address User Security
- Improve access policies compliance within mission critical applications
- Reduce implementation and upgrade costs with pre-configured roles
- Lower total cost of ownership by controlling changes to roles
- Avoid segregation of duties in ERP systems with proper role design
- Address user security but not create access violations
Fix Segregation of Duties Proactively
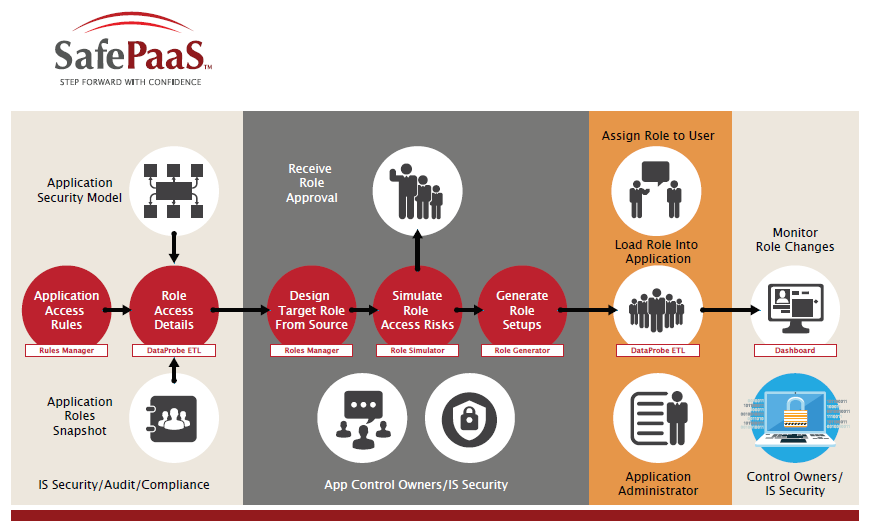
SafePaaS Roles Manager is an application security design tool that contains a pre-configured catalog of roles, which comply with access policies for Segregation of Duty and restrictive data access. You can use this tool to view existing role templates and design new roles by easily selecting or deselecting role configurations. Once the roles design is complete using workflows, it can be sent to pre-assigned reviewers and approvers to finalize the roles. The role preparers, reviewers and approvers can also assess the Segregation of Duty control risks before finagling the roles. Furthermore, these can be combined into composite roles that will match job responsibilities and comply with SOD policies. Our ERP Roles catalog contains Roles by ERP module and typical access requirements for those modules such as Manager, Supervisor, Clerk, Inquiry, Business Setup and IT Setup.
Our clients need an effective approach to design and manage the ERP security models to ensure compliance with Segregation of Duty and Sensitive Access policies. Our Roles Management tool enables our clients to remediate ERP security and control violations by addressing the root cause of the problem. This service rapidly improve access controls within mission critical applications while lowering the ERP total cost of ownership by using pre-approved Roles.
Capabilities
Analyze Role Entitlements Discover role entitlements by scanning access to application privileges and data using the security structure of your business application. Identify issues in access rights based on role assignments. Download analysis results in Microsoft Excel and determine remediation plan.
Detect risk of fraudulent, unauthorized, unusual and erroneous transactions within your business application to monitoring user activity. Audit database and application activities of all users granted privileges to perform critical business tasks such as maintain master data, update system configurations or access restricted information.
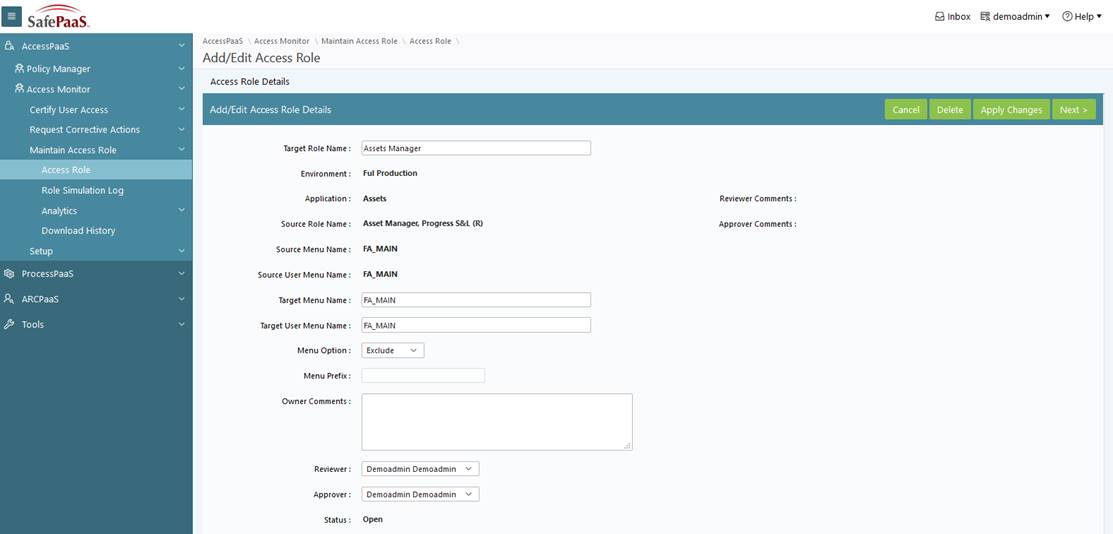
Design User Roles Improve application security and user productivity with effective role design. You can start by browsing through the catalog of role templates available in Roles Manager to select a template as a source and create a target role tailored for each job position. Each target role includes application specific access rights such as menus, functional and forms to deploy the target role.
Configure Role Entitlements Configure application security components by including new access rights to excluding existing security rights. Extend and customize security components such as menus, and permissions assigned to users within a role.
Control Data Access Limit user access to data by applying security rules, profile options and personalization based on data role, privileges, organizational unit and other security attributes available within the business application. Roles Manager can also be integrated with on-premise and Cloud ERP applications to deploy approved roles into the target systems, thereby reducing security design and risk remediation efforts.
Deploy Role Configuration Generate role configuration report to ensure that the target role meets business requirements. Submit the final role design to business application manager and access control owner for final review and approval. Execute role deployment steps to automatically load the role configuration into the business application.
Maintain Roles It is important to maintain change controls over the business application security model to ensure that the application control owners can review and approve any changes to roles based on business needs, organizational structure and user job positions. Roles Manager includes change control workflows to ensure that any changes to role design are reviewed and approved by authorized manager before releasing those changes for user assignment. Reports are available to track all changes to the role design as well as compare roles across application environments, business units, etc.
Provision Roles to User Streamline and control user-provisioning process to assign business application roles to users. Roles Manager enables self-service provisioning for new, as well as existing users. A user can request access to one or more roles online by select the application environment and submitting a workflow request to the pre-assigned role approver. The approver can receive the request via email with the option to approve or reject the request. The provisioning request and approval action are logged for audit reporting.
Grant Emergency Access Roles (Fire Fighter ID) Certain users require emergency access to sensitive functions to resolve technical problems such as errors in the financial close process. Users can request such access through the provisioning process. Once the access is granted, the user activity audit is activated automatically through approval of requested access via configurable workflow. Once active, all user activities are captured and stored as a complete audit trail. As needed, control owners, compliance managers and internal auditors are notified of any violations based on pre-defined thresholds. This control monitor mitigates privileged user access risks while maintaining flexibility and responsiveness required for business performance.
Certify User-Role Assignment Improve application security with periodic user access review and verification process. Roles Manager™ can send a user-role certification request via email notification to application access control owners to review active users and roles assigned to those users. You can detect and prevent any unauthorized user access rights and quickly correct any conflicts. A compressive report of the review and verification process is generated as evidence to support the effectiveness of your user access controls.

