Integrated fulfilment
Prevent Risks in ITSM User Request Management
Integrated Fulfilment – Prevent Risks in ITSM User Request Management
Today many businesses use ITSM tools to fulfil access requests using roles that are manually configured as catalogs. The downside: the manual management of roles at a high level created audit findings where the attribute level details in the business application do not accurately reflect in the Catalog role. For example, a role of Payables Inquiry available in ServiceNow does not prevent the risk of fulfilment where the user may also be granted access to the role in the Oracle ERP Cloud application that enables supplier creation – causing and significant risk to financial statements – enabling a user to create suppliers and pay suppliers.
Furthermore, the lack of integration with business application increases the risk where the access requests in the ITSM system do not match the actual user access in the business application where the access is granted within the application or through multiple provisioning workflows or systems,
SafePaaS enables integrated user request fulfilment to prevent fine-grained access violations.Enterprise-Wide Real-Time Fulfilment from ITSM
As users join the organization or change roles within it, SafePaaS rules and policy-driven fulfilment process manages the user access rights management within business applications with integrated ITSM services. User access is updated with authorized access for the approved start and end times, such as adding a user to Oracle Cloud ERP or SAP Hana S/4 and assigning authorized privileges through roles, and security attributes. SafePaaS ITSM integrated fine-grained fulfilment process improves organizational security posture and business productivity through accurate and timely fulfilment processes.
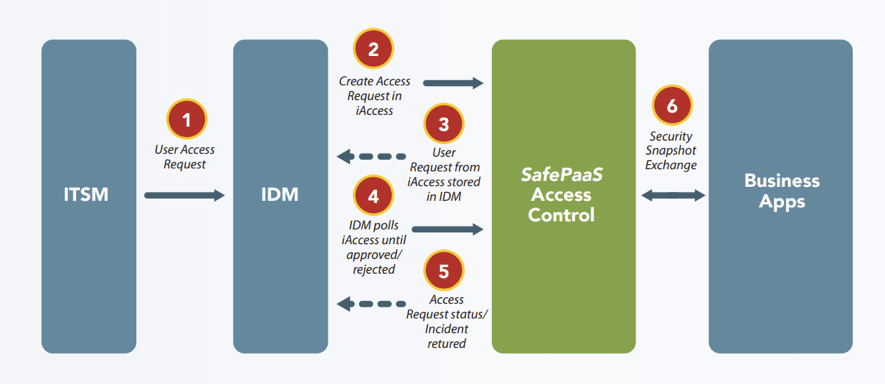
ITSM Access Request Control Analysis Prevents Policy Violations
All access requests that are submitted in ITSM for business application access are seamlessly initiated in SafePaaS for fine-grained controls analyses to ensure compliance with access governance policies. SafePaaS opens the ticket in the ITSM while syncing with SafePaaS for real-time ticket status. Once the request is received in SafePaaS, it is tested automatically against the policies and rules to detect violations and initiate additional workflows with violation analysis to control owner (that is usually not the immediate supervisor) for authorization. Once the request is either approved, rejected, or approved with waiver and compensating control SafePaaS fulfils the requests and the ticket is automatically updated in the ITSM. If access must be manually fulfilled, SafePaaS can assign the ticket to the ITSM. Workflow logic can be configured based on business needs.
Self-Service Access Request Controls
End-users can also simulate the risks in access requests in SafePaaS proactively to detect any potential access policy violations such as Segregation of Duties or Sensitive Access. If the access request is submitted with policy violations, the approver has the option to add mitigating controls to the SoD. This results in end-to-end controls over the access management process.
Recommended Reading

SafePaaS for ServiceNow
As a growing number of SafePaaS customers have adopted ServiceNow for IT service requests and workflows, we have introduced support for ServiceNow API services to rapidly remediate risks to ERP applications by automating closed-loop corrective actions in ServiceNow.

Fine-grained Access Certification
A comprehensive solution for automating every aspect of the access certification process at a fine-grained level. It is specifically designed to be easily integrated with Identity Management and IT Service Management solutions such as SailPoint, Okta and ServiceNow.

SafePaaS for SailPoint
In the last few years, business needs for effective access controls have evolved, beyond the general IGA capabilities in response to growing compliance mandates and increased cyber security risks. As a result, IGA customers are now demanding specialized capabilities based on new control objectives.

