policy-based access controls
Access Controls Governor
Any ERP :: Any Application :: Any Infrastructure
Control fine-grained identity access rights embedded in security roles to meet rapidly changing technology needs, compliance regulations, and cyber threats.
As organizations adopt an increasing number of business applications along with the expansion of data sources and devices, security risks are growing at unprecedented rates. Identity Governance and User Rights Management are more complex and the security design can impede the benefits of a modern digital business platform. Role-Based Access Controls (RBAC) available in ERP applications, Identity Governance, and IT Service Management systems are no longer sufficient to deal with the modern digital paradigm, especially when it comes to policy-based cross-application access management such as Segregation of Duties, User Access Request Orchestration, Periodic Access Certification, Privileged Access Management, and Data Protection.
Managing and controlling identities that grant users access to enterprise applications, databases, servers, and cloud infrastructure is challenging without effective policy-based access controls in place. Complex ERP security design can impede the deployment of a modern digital business platform without specialized solutions and knowledge.
Business needs for effective access controls have evolved, beyond the general IGA capabilities in response to growing compliance mandates and increased cyber security risks. As a result, IGA customers are now demanding specialized capabilities based on new control objectives to address the following gaps in the general-purpose IGA systems.
AccessPaaS™
A complete controls governance platform that seamlessly integrates with ERP applications, IT Service Management (ITSM), and IDM/IGA data sources to govern role-based access controls based on access policies at the fine-grained access rights level.
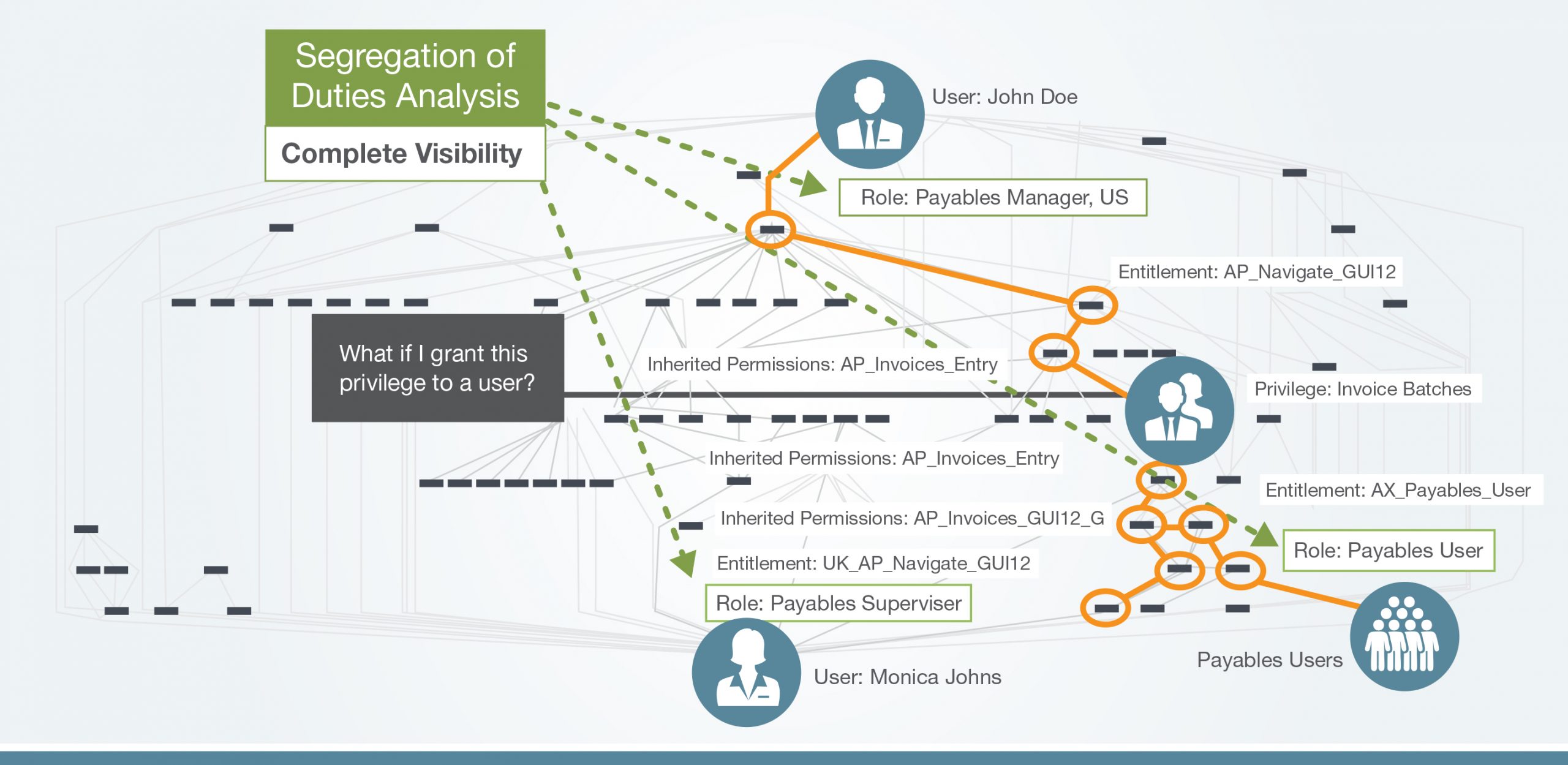
Detects access policy violations to control financial, operational, fraud, and cyber risks. Define policies in terms of risk descriptions, impact, likelihood, and fine-grained rules that constitute discrete and fuzzy logic in terms of IT system security entitlements and privileges for governance models such as Segregation of Duties, Sensitive Access, Data Protection, Trade Secrets etc. Eliminate false-positive filters to improve risk analysis and response. A high-performance policy engine rapidly analyzes millions of security attribute combinations and permutations across all enterprise IT systems and ERPs and business application security snapshots to report violations. Violation Manager eliminates exceptions where risk is accepted with compensating controls, using advanced filters. Remediation Manager issues corrective actions using closed-loop workflows that expedite risk response, reduce risk exposure and automatically update violations reports to ensure audit evidence is accurate and timely. We provide:
RULES MANAGEMENT
SECURITY SNAPSHOTS
VIOLATIONS MANAGER
FALSE POSITIVES
REMEDIATION
COMPENSATING CONTROLS
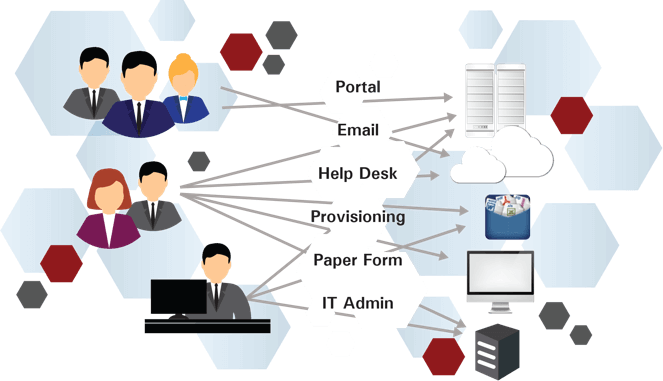
Traditional IAM
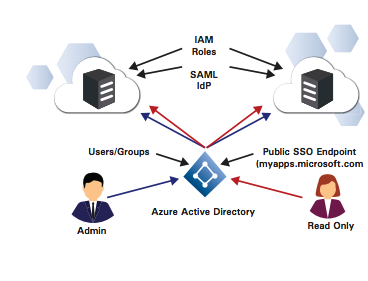
IAM with fine-grained capabilities
INTUITIVE REVIEW UI
CENTRAL MONITORING
SOAP / REST / JDBC
FINE-GRAINED CONTROLS
REMINDERS / ESCALATIONS
CHANGE REQUEST
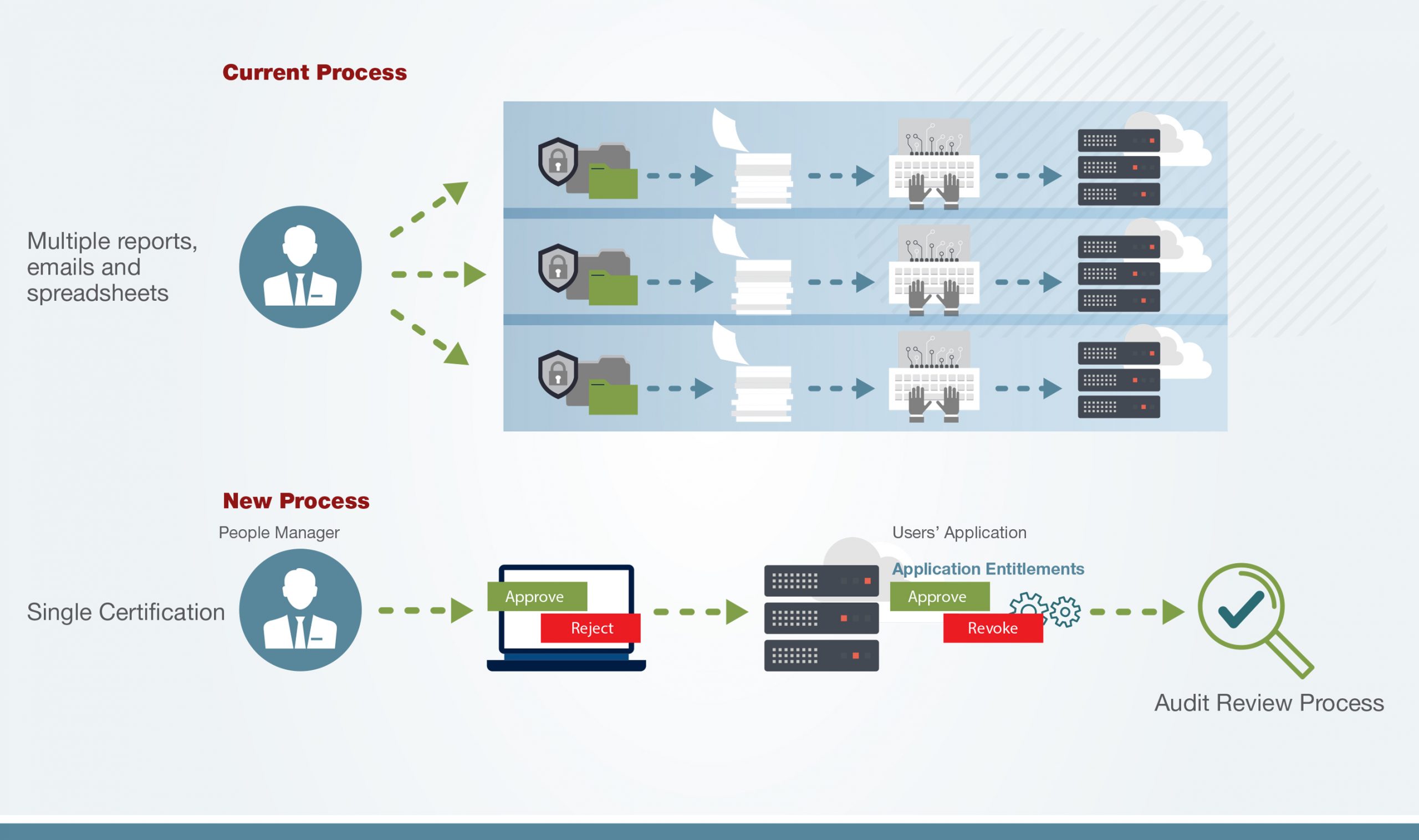
Access Certification Process with SafePaaS
Identity Orchestration – Identity Lifecycle Management
Today, organizations are facing an increasing demand for modern Identity life cycle management and analytics within identity and access management (IAM) platforms to detect malicious bots, prevent cyberthreats and monitor fraud risks without obstructing user productivity as they transition to more hybrid digital computing based on zero trust as the foundation of the digital enterprise
AccessPaaS™ Identity Orchestration enables consistent, policy-based identity and access to all your applications and infrastructure by levering your current investment in IAM tools like Microsoft Azure/AD, Okta, OneLogin, Ping Identity, IBM, Oracle, etc. You can analyze and control all identities in a distributed model across multi-cloud and hybrid cloud enterprise platforms. Policy-based Identity lifecycle management ensures that users have authorized access to apps running on-premises or on multiple cloud platforms — whether from the cloud or within the enterprise network -- modernizing your identity management process by serving as the orchestration hub allowing siloed identities and distributed policies across fragmented systems to come together for complete visibility.
Privileged user access is a necessity for managing most any IT application. Someone or a group must have the ability to maintain the application as needed to support the organization's business processes when issues arise.
SafePaaS FireFighter is a secure process for controlling super-user access across multiple systems with an independent system of record to provide an audit-trail for privileged or super-user access. SafePaaS enables pre-authorized users to request temporary access to elevated privileges to an organization’s business applications. The enhanced Firefighter request processing enables System Administrators or managers to grant immediate access to pre-approved users with assigned firefighter access to be able to get immediate access without any bottlenecks. The elevated access is logged and reported for management review.
Exponential growth in data volumes, and rapidly increasing attack surfaces are challenging security teams to control cyber threats and data leaks. Security data lakes can help address the key security challenges facing organizations.
The massive data generated from Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) solutions can take days to analyze and its cost prohibitive to store all the collected data which can cause key signals to be missed during an investigation or breaches to go unnoticed.
To overcome the challenges of scale, cost, structure, and detection capabilities, SafePaaS provides enterprise security data lake to separate storage from compute.
Don't know where to start?
Contact us for complimentary advice on where and how to start your access governance journey?

