
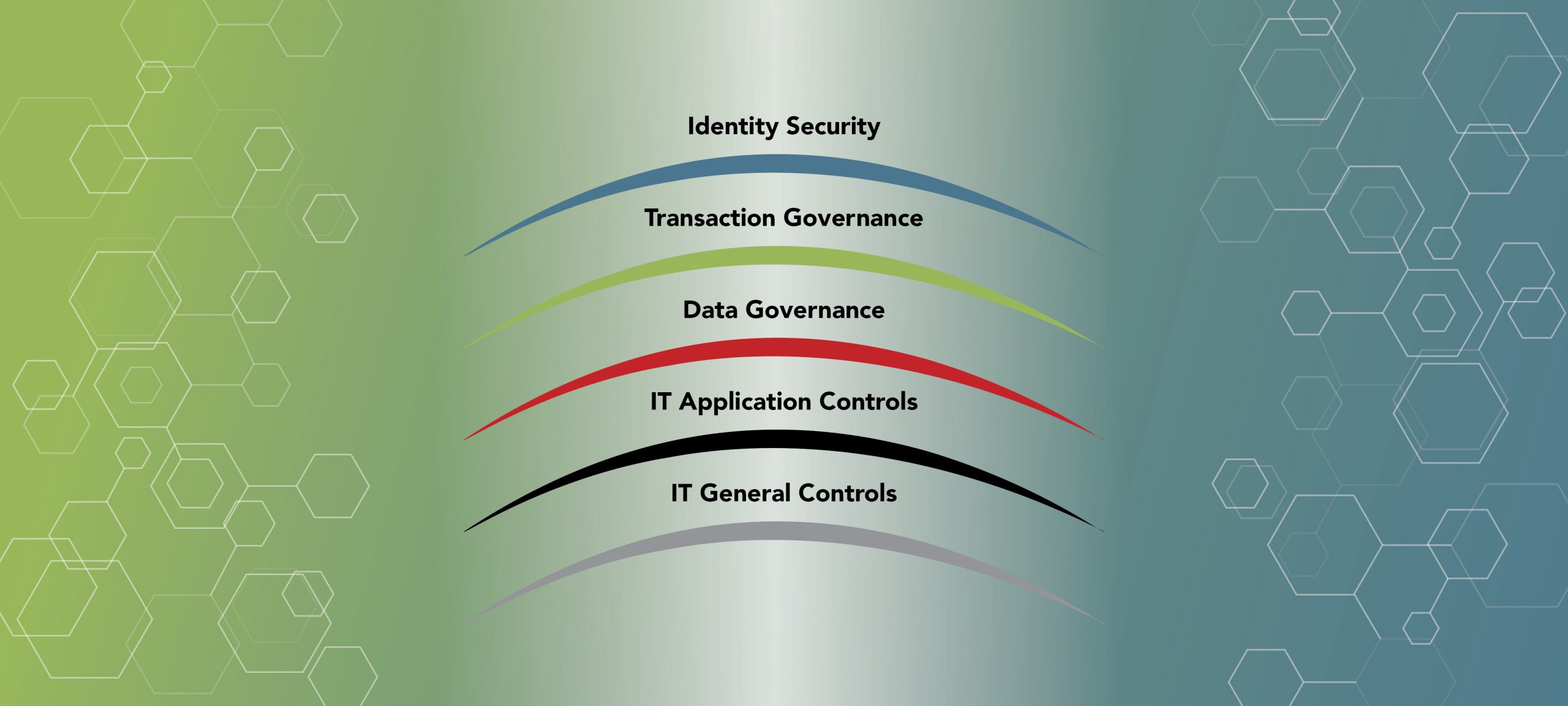
The governance control fabric that shields identity, transactions, data and applications across the enterprise.
Experience the power of automation with proactive workflows that seamlessly handle bottlenecks, escalations, and reassignment. Our active platform reduces manual intervention by automating control evidence gathering, remediation, and mitigation. With intelligent workflows and fast risk mitigation, your business is safeguarded at lightning speed, ensuring superior governance in today’s fast-paced world.
Empower Your Financial Integrity. Achieve enhanced accuracy, transparency, and trust with unbiased evaluations that uncover discrepancies and errors. Independent control evaluations ensure compliance, protect your reputation, and help you avoid legal penalties. With robust oversight, we identify fraud and financial mismanagement before they become threats. Make confident decisions and drive sustainable growth with the assurance that your financials are sound.
SafePaaS is built to adapt, seamlessly aligning with your evolving business needs, regulatory environments, and technical landscapes. Whether you’re scaling rapidly, moving to the cloud, or managing multi-application environments, our policy-based approach ensures access controls flex with your infrastructure, not against it.
SafePaaS provides a comprehensive solution for access governance. With full visibility and control across all identities, systems, and processes, you get end-to-end governance without the gaps.



Company type: Public Fortune 500
Industry: Food Retail
Primary ERP systems: Oracle E-Business Suite and Oracle ERP Cloud
Operating across 100 plus countries, our Fortune 500 customer faced the difficult task of aligning its IT controls with the Sarbanes-Oxley Act (SOX) IT General Controls (ITGC) requirements. With a complex IT infrastructure comprising on-premise ERP systems, cloud platforms, and numerous applications, achieving compliance presented significant hurdles.

Company type: Public
Industry: Fast food restaurants
Primary ERP systems: Oracle ERP Cloud
The organization is a well-known fast-food corporation that operates globally, with over 50,000 ERP users worldwide and a complicated network of applications, including Oracle ERP Cloud. The organization was facing significant challenges in managing Periodic Access Reviews (PARs) for Oracle ERP Cloud.

Company type: Public
Industry: Fast food restaurants
Primary ERP systems: Oracle ERP Cloud
The organization is a well-known fast-food chain that operates worldwide. To enhance Segregation of Duties (SoD) processes, the organization initiated a strategic effort to streamline compliance measures and minimize operational risks with SafePaaS. This initiative unfolded through a directed series of steps designed to promote alignment, reduce conflicts, and verify control effectiveness through robust audit analytics.

Company type: Subsidiary
Parent Company: One of Europe’s most highly valued tech company
Industry: Semiconductors
Primary ERP systems: Oracle E-Business Suite
A major semiconductor manufacturer specializing in producing and maintaining lasers for chip manufacturing worldwide realized it needed to improve its audit control activities and enhance operational efficiency. The organization faced challenges in monitoring transactions, enforcing restrictions on database changes, and the effectiveness of its audit oversight.

years combined access governance knowledge
Number of ERP users on the platform
Customer Retention Rate
Complex, reactive, and manual – slows down business and leaves security gaps.
Automated, intelligent, and policy-driven – secures access in real-time.


SafePaaS is the most widely used cloud platform for safeguarding enterprise businesses, ensuring security, compliance, and operational resilience at scale. But what truly sets us apart?
Industry-leading auditors rely on our platform to validate and enforce controls, providing assurance across regulatory landscapes.
We don’t just deliver cutting-edge technology—we drive real business impact. Our solutions and in-house services help organizations mitigate risk, improve efficiency, and achieve strategic objectives.
We connect effortlessly with your existing tech stack, including ERP systems, IDM, ITSM, and HR platforms, ensuring a unified and automated workflow.
Strengthen security with fine-grained Segregation of Duties enforcement.
Cut compliance fatigue and manual work by automating access reviews. Instantly validate user permissions to ensure the right access for the right people, with fine-grained, real-time visibility.
Effortlessly manage access as users join, move, or leave – automatically enforcing segregation of duties with every change, ensuring security without the hassle.
Control and track high-risk permissions to prevent breaches, fraud, or abuse by insiders.
Safeguard your business operations against cyber security risks and insider threats from access policy violations.
Ensure updates and modifications are properly authorized, reducing the risk of errors, fraud, or compliance violations.
Thank you for reaching out. If you have any questions, inquiries, or require assistance, please don’t hesitate to contact us using the form below. A member of our team will respond to your message as promptly as possible.
