Real-time insight
Advanced Access Analytics
Security Risks and Policy Violations Analysis
Access Analytics is a key component of an enterprise access governance solution as it can improve the effectiveness of controls and provide real-time insight to mitigate emerging threats. SafePaaS customers use access analytics in many ways and rely on results to safeguard their business against cyber security risks and insider threats from access policy violations.
Analytics is also a catalyst for digital strategy and transformation as it enables timely and more accurate design of the business roles and application entitlements in complex and fast-changing business contexts to optimise productivity.
Today’s data-driven enterprise can leverage the Identity data stored in the information system using SafePaaS analytics to ensure successful digital transformation including policy-based access governance for sustainable value creation.
Analyze security threats to business applications and IT systems.
Organizations require proactive and periodic analysis of growing threats to business applications and IT systems to support hybrid, agile and hyper-automation business needs. The traditional business intelligence and reporting tools are unable to cross-link changes to complex security meta-data against the fragmented, de-centralized provisioning process. Effective analysis requires not only the privileges assigned to employees, but also third parties, service accounts and BOTs to ensure compliance with access governance policies.
SafePaaS Advanced Analytics enables you to “find the needle in haystack” by using discrete as well as fuzzy logic to filter historical data sets stored in SafePaaS, and perform What-if analysis to predict potential risks that would impact business applications and IT systems. Advanced data comparison options ensure that requested corrective actions to security are completed timely. Changes introduced by third-party application providers are detected and alerts are routed to IT security personnel for examination and remediation. Auditors can ensure that access controls are operating effectively by analyzing ITSM request logs against the fulfilment records in business and IT systems. Application administrators can ensure that the user access to applications is terminated when employee jobs assignment are changed or terminated in HR systems to prevent orphaned or dormant access.
Here are some of the popular analytics SafePaaS customers use to monitor access risks in their business applications:
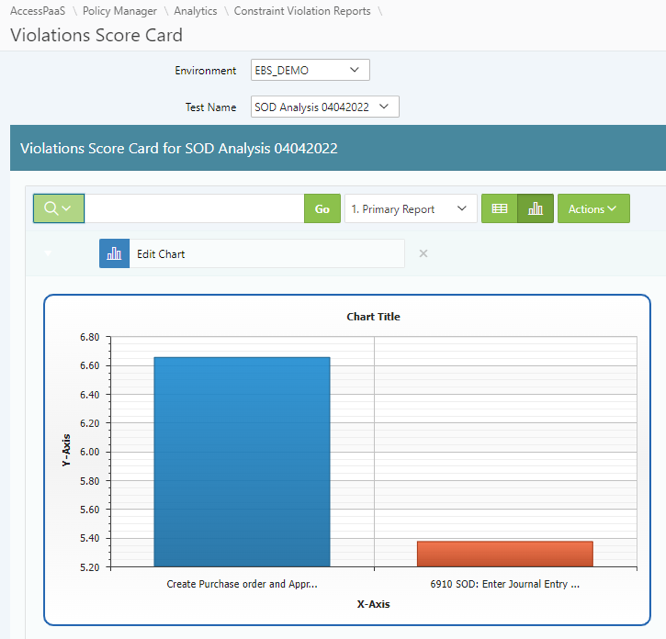
Access Score Cards - Provides a summary of access risks by policy, business unit, and application. The report can be viewed in tabular form or graphed using standard functionality available throughout the platform. Frequently used by executive management to assess the overall access risks and monitor progress against the remediation plans.
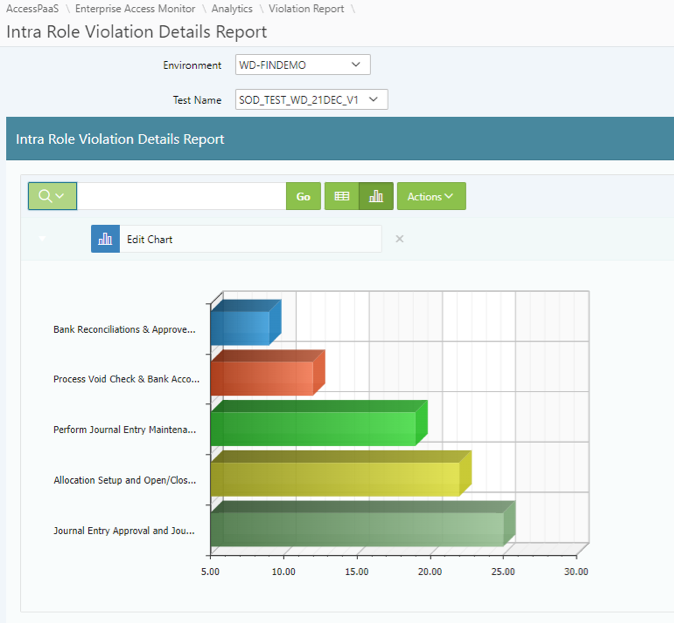
Intra-Role Inherent Violations - Provides inherent risk in the business role configurations, including the component and attribute details that grant privileges to the role. Frequently used by application administration to redesign and reconfigure out-of-the-box roles provided by application vendors that don't comply with access policies.
User Violation Details - Provides user details, roles, groups, and conflicting access path details that violate access policies. It includes directly granted privileges, as well as inherited privileges, data group permissions, and other overriding attributes defined in the security model. Frequently used by IT security and compliance teams to analyze violations, prepare remediation plans, or accept risks with compensating controls.
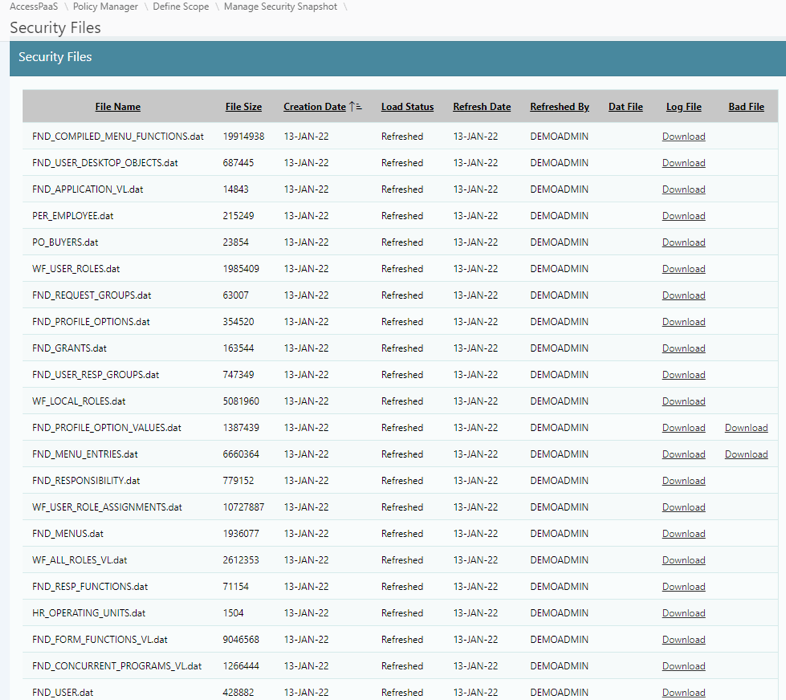
Security Snapshot - Provides comprehensive visibility into continuously changing security snapshots of business applications. Security analysis is frequently used by application administrators to analyze changes to role configurations, user assignments, new security attributes introduced by application vendors, changes in organization structure, and deployment of new functionality.
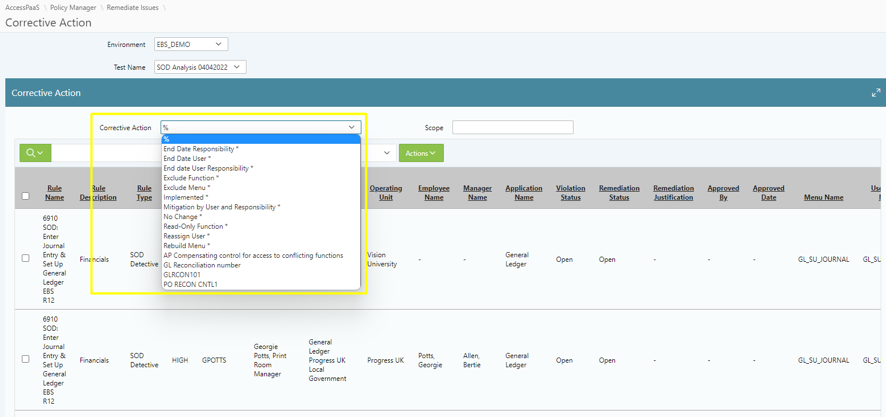
Remediation Management - Provides detailed status of corrective actions workflows by action type such as request to change assignments, reconfigure roles, or modify access control attributes within the security model such as data groups, profiles, business units, and authorization limits. Control Owners and IS security teams use these reports to ensure the remediation plan is completed on time and results are verified.
Advanced Analytics enables Lookback Audit to assess Materialized Risks
Auditors require look-back analysis, to review prior-period evidence to evaluate the effectiveness of access controls management process by detecting incidents where the potential risk detected during the audit analysis may have materialized.
For example, Segregation of Duties (SoD) controls analysis identifies the users that can violate one or more SOD policies. Once the violations are detected, and the majority of the risk is remediated or mitigated by fixing security roles or changing user access assignments, the remaining unmitigated “residual” risk requires lookback analysis. Residual risks exist in the majority of the complex ERP systems because the remediation process is labor intensive and costly or it requires the organization to make changes to the process or increase in personnel - which is time consuming and over the budget. Residual risk requires auditors to perform lookback analysis to detect user that performed conflicting activities where the risk was not mitigated. For example, if users in the payable department had the ability to Create a Supplier and Pay a Supplier, how many of those users actually performed such transactions during the audit period. This analysis qualifies Segregation of Duties risks by identifying and quantifying the financial exposure from SoD violation transactions e.g., creating a supplier and paying that same supplier. This type of analysis, historically a monumental task, can be automated with SafePaaS Advanced Analytics.