NetSuite
NetSuite Security Model
How you can use SafePaaS solutions to secure your NetSuite environment
If you are considering implementing or upgrading NetSuite, you should look at SafePaaS to help with risk mitigation. Risk is all about completeness so we recommend taking a proactive approach to address security risks such as segregation of duties conflicts.
A proactive approach to NetSuite security should include:
Define segregation of duties policies
Design Roles leveraging a tool such as Roles Manager that are free from segregation of duties conflicts
Ensure roles are segregation of duties conflict-free before they get assigned to users
Go through User Acceptance Training before go-live
Taking a proactive approach to NetSuite security early on in the project and using SafePaaS platform will allow organisations to reduce risk, and ultimately save both money and time.
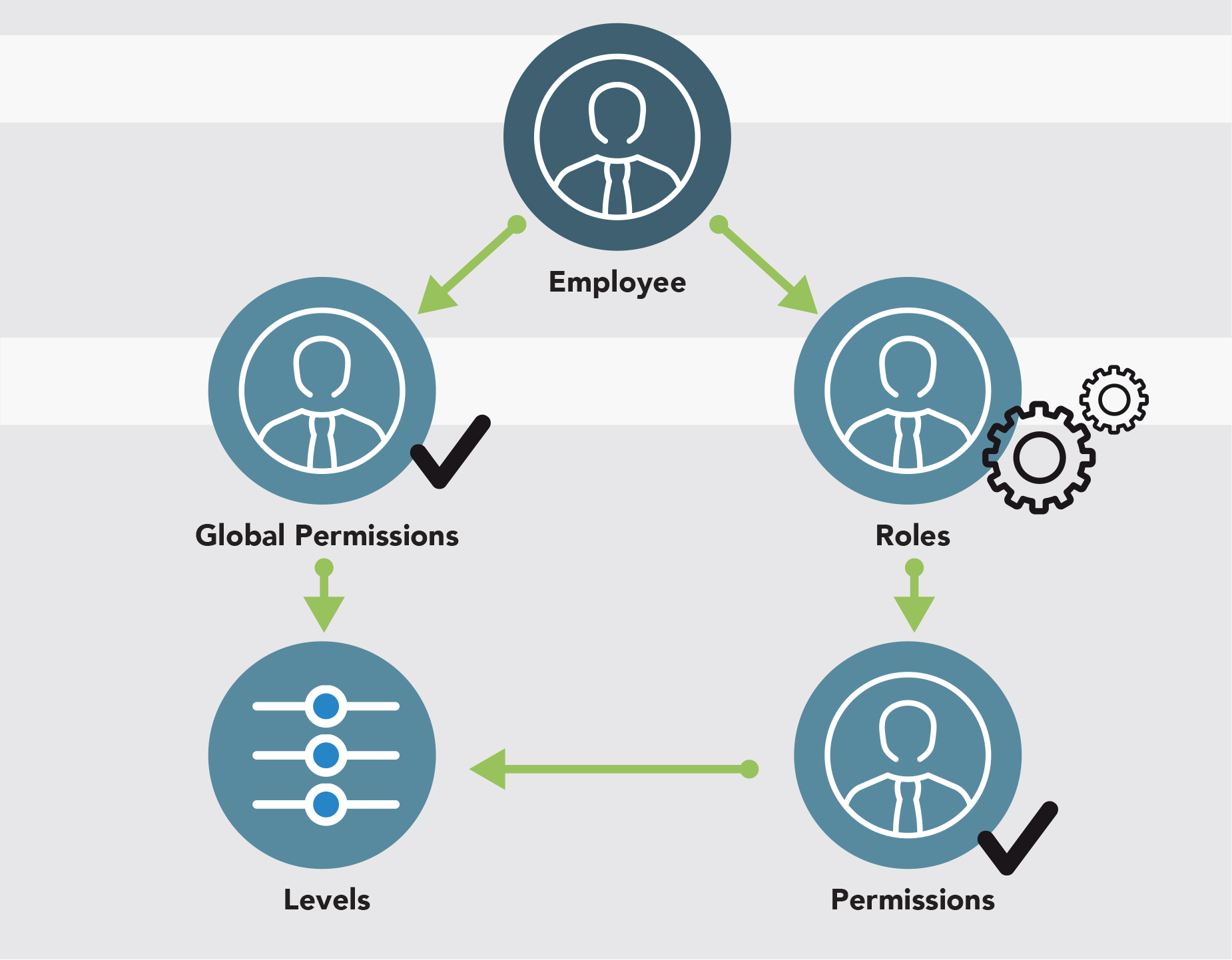
A NetSuite User is an individual who has access to a single or multiple NetSuite accounts. Access to different accounts is directly related to an email address. An employee is the most common entity that has access to NetSuite, however, vendors, partners, and customers can also be users.
A Role is a defined access configuration that can be assigned to users. Each role includes a set of associated restrictions and Permissions that determine the data users can see and the tasks they can perform.
A Permission is defined by an access level which determines what the user is allowed to do regarding the specific permission.
Global Permissions that apply across all of their assigned roles. This is a native NetSuite feature; however, it is not enabled by default. When there are conflicts between a global permission access level and a role permission access level, the global permission will take precedence.
Improve Business Performance with Application Assurance:
NetSuite Security Model
Here are some examples of challenges that can be solved with our Smart Controls Cloud:
Which Segregation of Duty (SOD) Policies will mitigate the risk in User Roles
Cannot use “seeded” Roles and Responsibilities because of inherent SOD conflicts
How to ensure that the activities of users granted “super user” responsibilities have effective compensating control
Why there are so many False Positives and how to remove them from your analysis
When all SOD incidents will be able to close
Functionality worked in Dev but not in Prod
App functionality works in old release version but not in the new release
App setups are changed without authorization
Not able to validate setups to auditor or business
App is no longer functioning properly and there’s no record of what changed
The system configuration documentation is out of date
Applied a patch and full impact not known
App customizations are lost or broken after upgrading to new release
Had project overruns and production downtime
Missed deployment milestones for rollouts and upgrades because of manual effort

