Privileged User Access Management in Oracle EBS


The Threat: Privileged User Abuse
Privileged user access is a necessity for managing most any IT application. Someone or a group must have the ability to maintain the application as needed to support the organization business processes when issues arise. This blog explores how to prevent Privileged User Access Risks in Oracle E-Business Suite with SafePaaS Privileged Access Management solution FireFighterID™.
Numerous situations occur where an organization needs to grant “superuser” access to employees under unusual circumstances. These are instances of “exceptional access” that fall outside the user’s typical job role or responsibilities and will typically create access policy violations that need to be highly supervised. Despite the need, access privileges that create risks, such as segregation of duties conflicts, need to be mitigated and requires the maintenance of an audit log of all superuser access activities in order to satisfy regulatory compliance requirements. But this level of Privileged Access comes with risks, these are several examples of risks where actual malfeasance has been determined.

Privileged User Abuse
Chief Information Officers are keenly aware of the threat not only to their intellectual property, but ultimately to their bottom line.
- According to Association of Certified Fraud Examiners fraud survey, $348billion a year in corporate losses can be tied directly to privileged user fraud.
- In a recent survey conducted of IT practitioners Ponemon Institute showed 45% of respondents believe the threat will continue to grow and another 43% believe it will remain the same over the next 12-24 months.
- An employee with privileged user access, at a U.S. based global energy company, was enticed by a foreign company, to steal source code and other intellectual property from his employer. As a result of his theft, the energy company lost three quarters of its revenue, half its workforce, and more than $1 billion in market value.
The challenge is while Privileged Access is necessary, it needs to be determined to what degree and how organizations manage this need and minimize risk. Too much access has been the typical response which obviously increases Privileged Access risk.
As an organization, SafePaaS has developed controls monitoring user access that can be extended to Privileged Users and SafePaaS’ FirefighterID™ capabilities are able to prevent and monitor this level of access in a more effective manner.
Who are Privileged Users?
Damage caused by privileged users is the most extensive, the hardest to mitigate and the hardest to detect as it is done by authorized users doing things they are authorized to do.
They are often very technically savvy and have elevated access to systems, making it easy for them to cover their tracks.
So, who are they?
- Database Administrator
- System Administrator
- Network Engineer
- IT Security Practitioner
- IT Audit Practioner
- Data Center Operations
- Application Developer
- Cloud Custodian
The challenge is how to provide the level of access needed for these users to effectively manage the applications to address issues as they arise, while not impacting organizational operations, and also minimize risk with Privileged Access users.
Standard ERP Access Controls
Below is the Oracle E-Business Suite user provisioning screen showing the steps to provide a user Privileged Access capabilities, (concept is the same regardless of application).
As you step through the setup, there are key areas of risk. In this example; no resetting of passwords, indefinite access and what access are they assigned through responsibilities.
Most organizations setup these users without any restrictions or monitoring which causes Privileged Access risks. Organizations today are looking to do a better job of controlling and limiting this level of access.
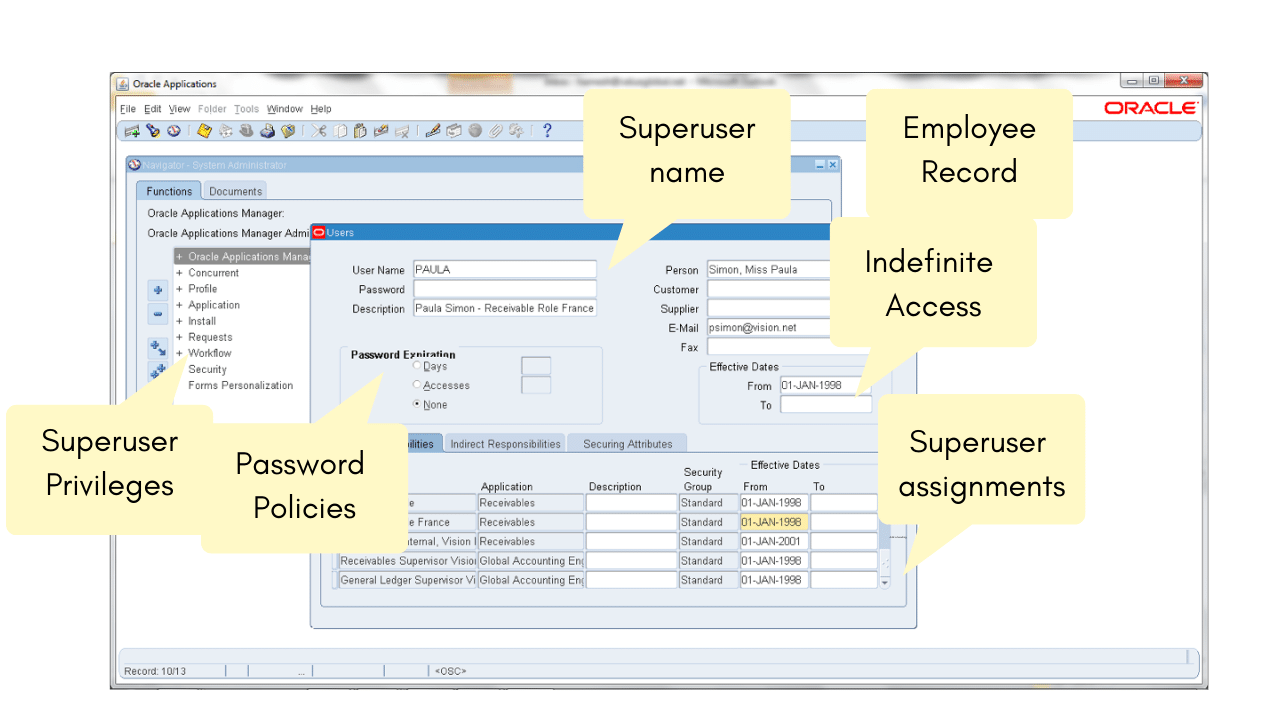
Standard ERP User Access Controls are infective for Privileged User Management
ERP User Provisioning Process does not mitigate super user risk.
- Not revoking privileged access status after the employee’s role changed, and providing everyone at a certain level in the organization with such access.
- IT operations is primarily responsible for assigning, managing and controlling privileged user access rights. However, business units and IT security are the functions most often responsible for conducting privileged user role certification.
- Privileged access rights that go beyond the individual’s role or responsibilities are often assigned.
- There is an inability to create a unified view of privileged user access across the enterprise.
Privileged Access cannot be managed effectively through the standard provisioning process. Typically, once Privileged Access is given to a user, it is not revoked; creating a high level of risk. De-provisioning occurs either manually or automatically when someone leaves the organization; Privileged Access users aren’t affected by that process.
IT is the part of the organization that manages Privileged Access, but IT is typically monitoring this level of access; so they are monitoring themselves.
Privileged Access typically goes beyond the assigned individuals needed access to address the issue. It is difficult to determine what level of access a Privileged Access user needs to address a pressing issue. In most cases, Privileged Access users are given more access than they really need.
Every organization is different, making it difficult to create a single unified view of Privileged User Access, and how to manage this level of access. Organizations typically have many business processes with each process having unique functionality requiring a detailed understanding of each application. Because of the complexity, Privileged Access is typically assigned to more than one person, so establishing a single PA is unattainable.
The Business Case for improving Privileged User Access controls
Identity Governance Business Case
Identity governance is the policy-based centralized orchestration of user identity management and access control.
- Cybersecurity risk is increasing with the adoption of Social, Cloud and Mobile which is uncharted, unregulated and faces few restrictions.
- Organizations must improve Identity Governance to safeguard against data breaches, theft, fraud, sabotage, and other security risks.
- The User access request process in many ERP Applications is inefficient and inconsistent where users are granted access without necessary policy checks and approvals.
- The User provisioning process can be improved by consistently enforcing access policy, such as segregation of duty (SoD) rules, before violations get introduced into the ERP environment, controlling sensitive business information to potential threats and vulnerabilities.
There is a clear business case for improving Privileged User Access controls;
Changing technology where Identity Management is becoming more of a risk concern. Many organizations are deploying multiple applications such cloud, on-premise, custom applications...Privileged Access needs to be managed for each mission critical application where fraud may have a significant impact on the organization.
Most organizations' provisioning process is very unstructured with emails, phone calls, ticketing systems that don’t provide an auditable consistent process. This is compounded with Privileged Users due to the level of access and related risks. There is a need to enforce policy management within the provisioning process; the more you can automate the more predictable and effective it will be to manage.
With automation and focus on access management, you can improve the provisioning process with policy evaluation and workflow approvals to prevent introducing risk to the organization. SafePaaS FirefighterID™ capabilities help improve management and monitoring of this level of access.
The below infographic represents the provisioning process using SafePaaS iAccess™ which is slightly different for Privileged User Management.
The first swim lane identifies the access policies and source for users to be provisioned, they come from your other onboarding processes such as Active directory, HR, IDM...
The second swim lane provides for the following; only registered users are allowed access, manager or through self-service users request access to the ERP. Once the request is initiated, the process for policy violations (step 1) is started. Upon completion, the approval workflow is initiated to ensure all approvals are provided for the request.
The third swim lane shows how the user is updated based on workflow approvals (if desirable) for roles requested in the ERP.
To close the loop for Privileged Access, certification is initiated with MonitorPaaS™. MonitorPaaS™ provides a report of the FireFighter Access as to which applications were accessed by the user and what functions they may have executed; establishing a monitoring control over this level of access.
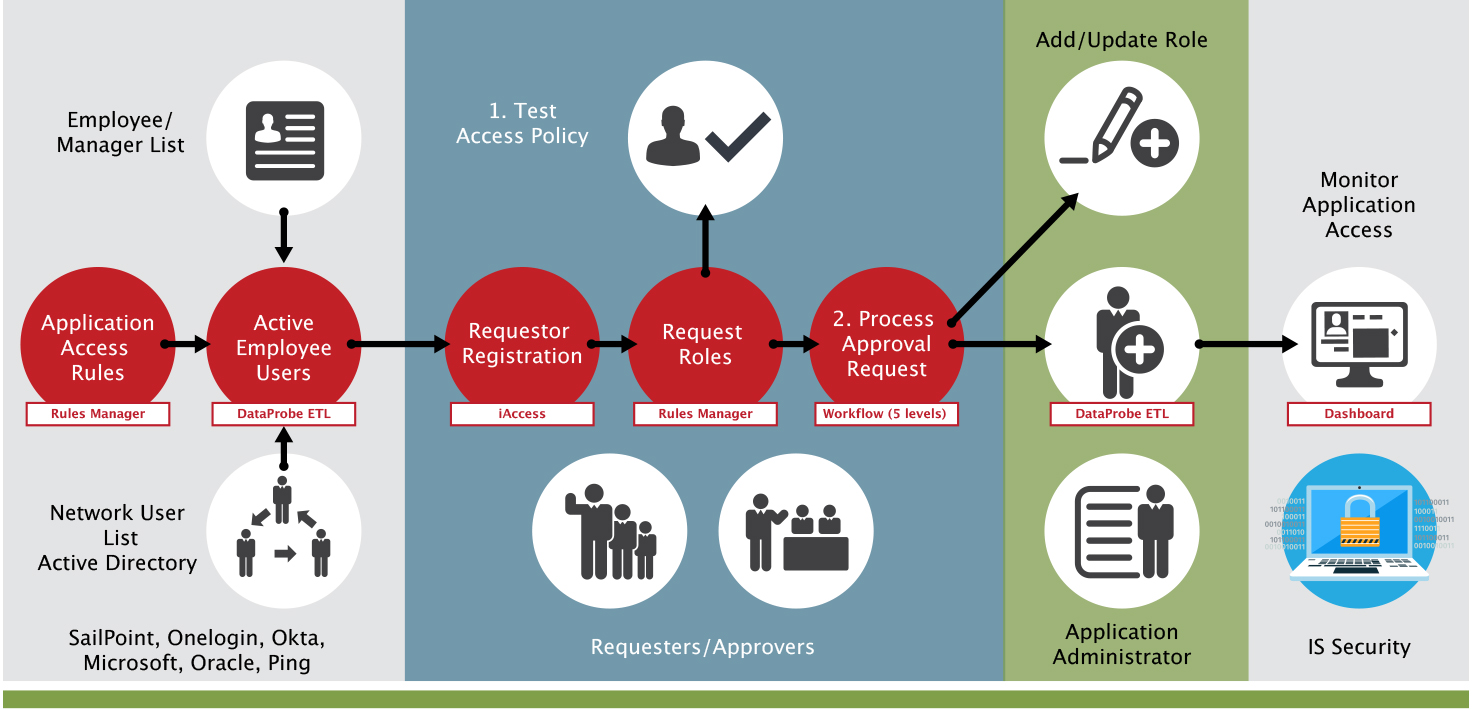
Prevent access risks in user access request
This second infographic represents how to control superuser access.
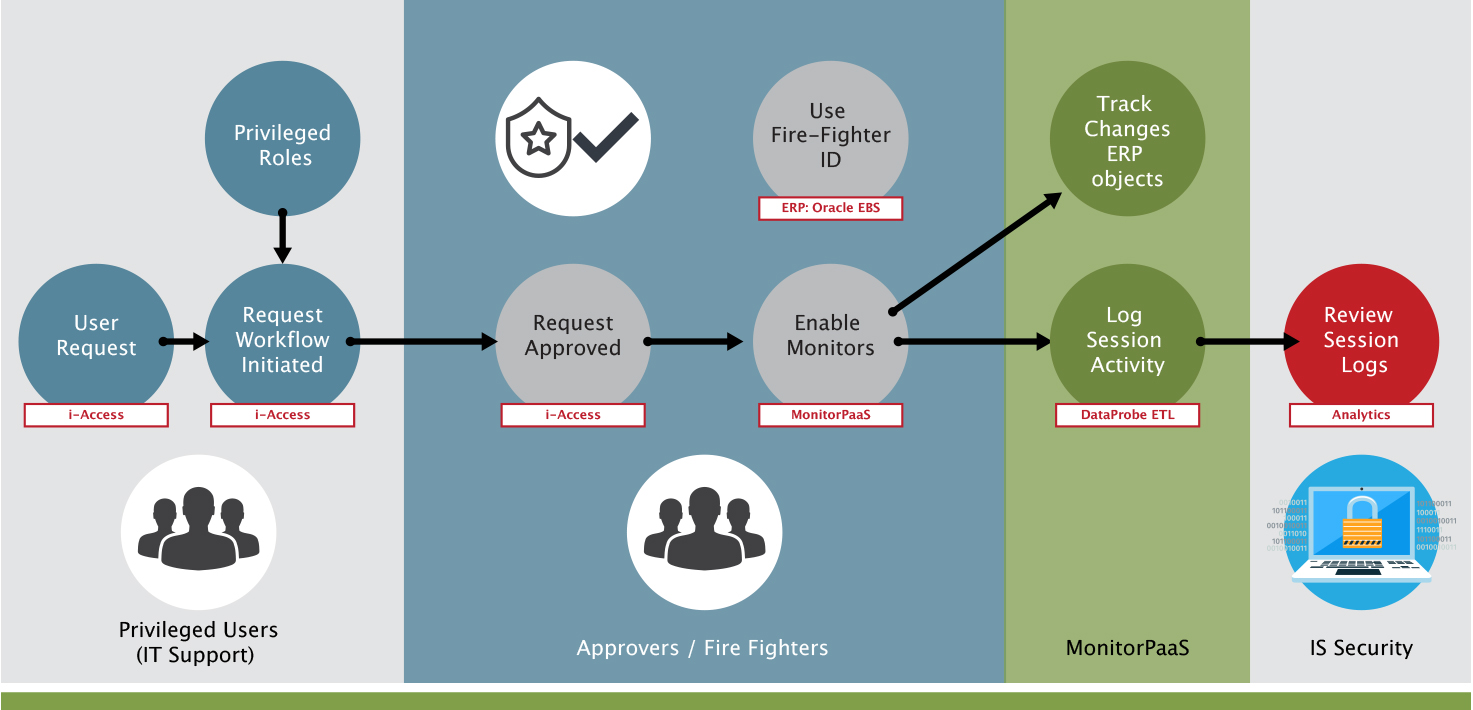
Control Superuser Access
Watch the Power of SafePaaS
See why the word's most complex organizations are using SafePaaS to truly mitigate risk across the whole enterprise.
More blogs you may be interested in...

Top 5 Reasons to Automate Controls
Application controls apply to the business processes they support. These controls are designed within the application to prevent or detect unauthorized transactions. When combined with manual controls, as necessary, application controls ensure completeness, accuracy, authorization and validity of processing transactions.

Top Technology Risks of Outdated GRC Software
In the last decade, the need to integrate GRC on a unified platform was realized by many organizations to streamline functional areas of GRC under a single platform.

Why automate User Access Review
User Access Reviews, also known as Access Certification and Periodic access review is an essential part of access management to mitigate risk. Unfortunately, many organizations view user access reviews as a “check the box” audit exercise and fail to realize the many benefits of automating the process.

