Automation
Policy-based Access Life Cycle Management
Empower users to streamline workflows
Digitalization and the constant evolution of business and IT landscapes together with the increased adoption of hybrid work models, hundreds of cloud applications along with legacy on-premise applications have materially increased the risks in user access request management.
Organizations with complex enterprise systems, require Identity Life Cycle Management solutions to control access for onboarding employees, contractors, and third parties. Any change to work assignments, or departures from the organization requires immediate updates to security privileges in compliance with access governance policies to ensure users only have access to what they need while removing access they don’t need. Policy-based access management also improves user productivity while preventing unauthorized users from accessing business-critical systems.

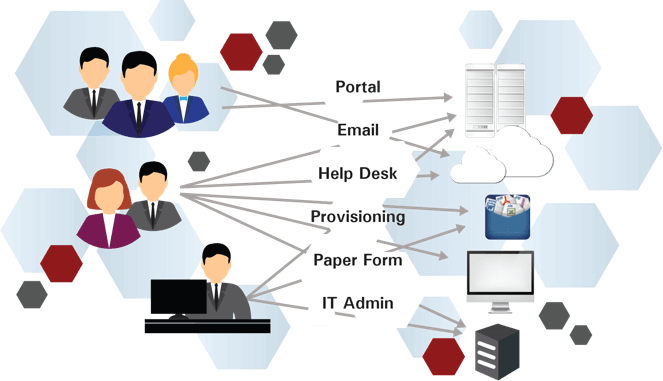
iAccess™ automates the Identity Life Cycle Management processes for organizations seeking to improve productivity, agility, and responsiveness. It can be deployed as a self-service access request management solution to ensure that user access service requests are managed in a streamlined manner. It can also be integrated to receive access requests from a wide variety of methods and sources such as ITSM and IDM systems. It reduces IT help desk costs and errors by efficiently managing the volumes of access service requests by enabling an integrated, process-based, best practice framework for managing access request services, which specifies that along with the service desk, service requests must be managed by the request fulfillment process.
SafePaaS iAccess™ solution includes advanced flexible options to empower users to streamline their workflows to provision users and identities according to policy-based access controls. Management can gain real-time fine-grained visibility into user and identity behavior across the entire enterprise.
Look familiar?
Provisioning All Users According to Policy
Enable Policy Based Self Service User Access Request Management
Prevent Segregation of Duties risks and on-going remediation costs as new users are on-boarded
Reduce help desk workload, eliminate manual steps and improve provisioning time with integrated user request management
Lower the cost of compliance and audit fees by ensuring that all security privileges assigned to users have a multi-level approval audit trail of user access requests
Improved your compliance audit trail
Reduce the risk of internal fraud
Why SafePaaS iAccess™
Lower the cost of compliance and audit fees by ensuring that all security privileges assigned to users have a multi-level approval audit trail of user access requests.
- Consistently apply access / segregation of duties policies to all roles
- Automatically approve and verify exceptions
- Maintain universal access security compliance
SafePaaS ensures that provisioning requests are checked against SoD policies before allowing role assignment. Exceptions that require management approval are processed via workflow notifications to obtain electronic approval from authorized supervisors. Utilize iAccess™ User Provisioning during ERP implementations or upgrades to help your process owners establish and assign roles without violating application access controls by pre-testing new or revised user security models.
- Lower cost of the provisioning process leveraging automation across multiple applications
- Eliminate manual processes that take hours to perform
- Complete audit trail of all approvers and reviewers status and updates
- Prevent introducing segregation of duties violations into the ERP with new users or additional access
- Reduce audit effort and risk to ensure compliance with policy-based access controls
Recommended Reading

Streamline Fragmented User Access
The cloud is making it more cost-effective to roll out applications because of the ease of connecting to the cloud. However, having so many applications is causing a problem of fragmented access.

Policy-based IGA for Oracle
SafePaaS already comes with out-of-the-box segregation of duties policies for all these Oracle applications and provides enhanced IGA capabilities and Identity Orchestration to offer deeper capabilities for segregation of duties in access request management.

How to control user provisioning
As organizations adopt hybrid work models and become more complex, taking a smart approach to access management especially in ERP systems is critical to truly mitigating risk. Traditional IGA solutions work at such a high-level, they can’t look into certain controls such as preventive segregation of duties.

