DataProbeETL™ - Secure Data Integration
Assess Access, Transaction and Configuration Risks in your Business
- Identify access risks that may lead to fraud or data breach
- Detect policy violations in business applications that cause loses
- Discover opportunities to improve business operations
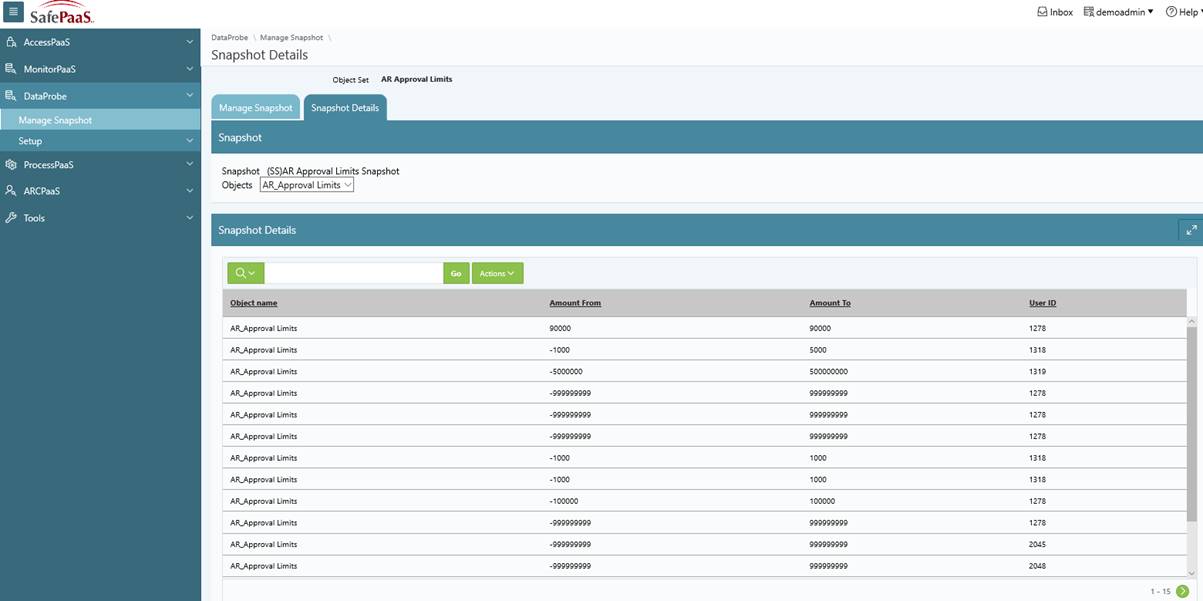
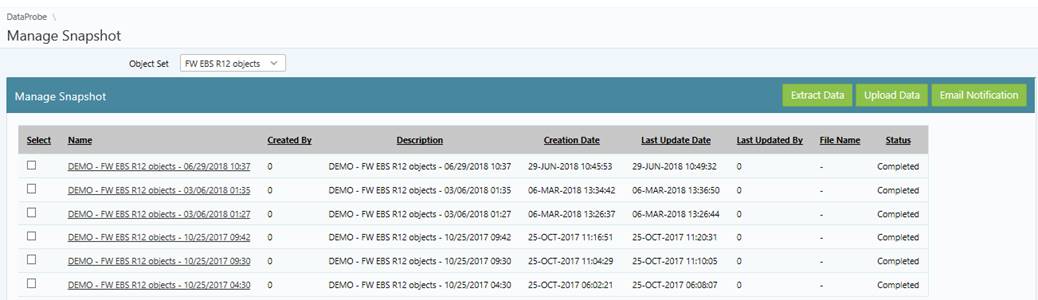
DataProbeETL™ is data discovery tool that enables you to assess the integrity of enterprise data by testing all direct access to enterprise data. With the DataProbeETL™ , you can identify unauthorized access and changes to the data stored in ERP systems, data warehouses, document management repositories as well as cloud applications such as Oracle Fusion, Salesforce and Workday.
The information stored in enterprise databases is growing exponentially and increasingly sensitive. Enterprise information assets must be safeguarded to maintain strategic advantage and comply with regulatory policies such as SOX, PCI, HIPPA, EU Data Directive, etc.
You can use DataProbeETL™ to identify data access from ERP systems as well as direct access from applications such as TOAD, Microsoft Excel, DB Links, JDBC, ODBC or other direct connections to the database that bypass any monitoring controls.
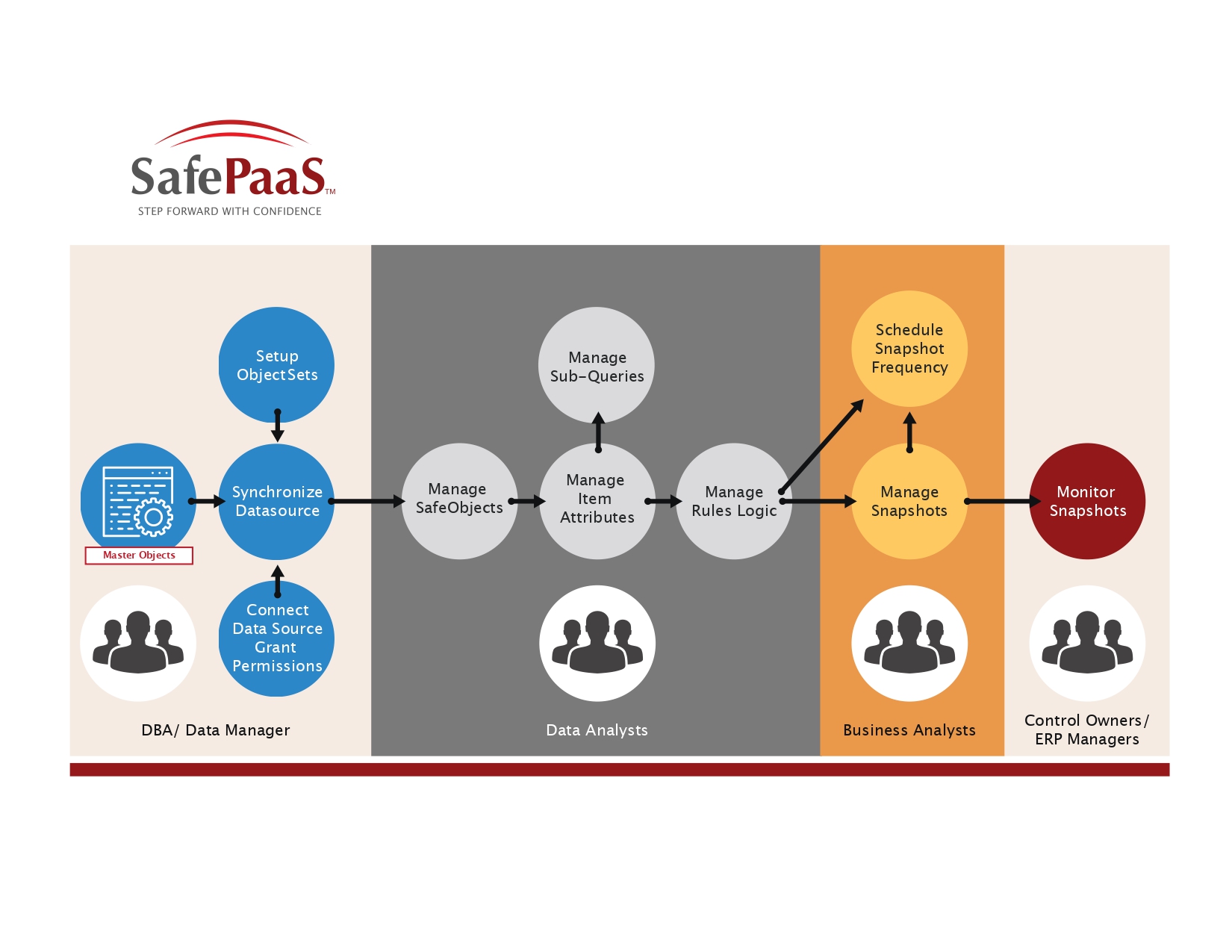
DataProbeETL™ is an advanced analytics tool that will help you assess risk from unfettered access to enterprise database such as:
- Inappropriate or unauthorized modifications of database schema, for example, copying sensitive data from an audited table to a hidden table that does not trigger any monitoring
- Changing access privileges or using a dormant account to modify data, and then resetting the access privileges so avoid detection of inappropriate activity
- Using legitimate application user accounts such as “APPS” in Oracle E-Business Suite to access or update data without detection
- Unlimited access to high volumes of data or access outside normal business hours without any business justification
We enable Database Administrators, Security Officers and Risk Managers:
- Identity unauthorized data access from ERP systems and direct access tools
- Detect misconfigurations in ERP systems, and inconsistencies in master data
- Discover transactional errors and bottlenecks based on patterns and exceptions

