Zero Trust Security Guide for the Digital Enterprise


Zero Trust Security Guide for the Digital Enterprise
The growing severity and frequency of data breaches and cyberattacks expose the reality that current security strategies are ineffective in combatting modern cyber threats.
In an era of increasingly sophisticated attacks, traditional security approaches that rely on perimeter defense are no longer enough. As your organization embraces digital transformation, adopts cloud technologies, and facilitates remote work, a new security framework is needed that challenges the conventional notion of trust.
This guide explores the concepts, principles, use cases, and benefits of Zero Trust, shedding light on how it transforms traditional security models and empowers organizations to safeguard their digital environments more effectively.
Identities are the new perimeter. To ensure your organization's security, you need a Zero Trust security model to protect your data, systems, and access points.
What is Zero Trust?
Zero Trust is straightforward: Trust no one and verify everyone. The Zero Trust security model considers all identities to be a threat. A Zero Trust framework enhances cybersecurity by challenging the traditional perimeter approach of trusting everything inside the network. In a Zero Trust model, every user, device, and application inside or outside your network is untrusted until proven otherwise. Zero Trust aims to minimize and reduce your attack surface by implementing stringent access controls, continuous monitoring, and multi-factor authentication.
Key principles of the Zero Trust model
Key principles of Zero Trust include:
Identity-based access: Users and devices are authenticated and authorized based on their unique identities rather than relying solely on the network location.
Least privilege: Access rights are granted at the minimum level necessary to perform specific tasks or access specific resources, reducing the potential for lateral movement and limiting the impact of a breach.
Micro-segmentation: Network resources are divided into smaller segments, enabling granular control over data flow and minimizing the ability for attackers to move laterally within a network.
Continuous monitoring: Ongoing user and device behavior monitoring are crucial to detect and respond to suspicious activity or deviations from normal behavior patterns.
Multi-factor authentication (MFA): Strong authentication mechanisms, such as MFA, are implemented to ensure the identity of users and devices.
Encryption: Data is encrypted both in transit and at rest to protect it from unauthorized access.
By adopting a Zero Trust strategy, you can better protect your organization's digital assets, prevent unauthorized access, and mitigate the impact of potential security breaches. It emphasizes the importance of robust authentication, strict access controls, and continuous monitoring to ensure a more secure and resilient environment.
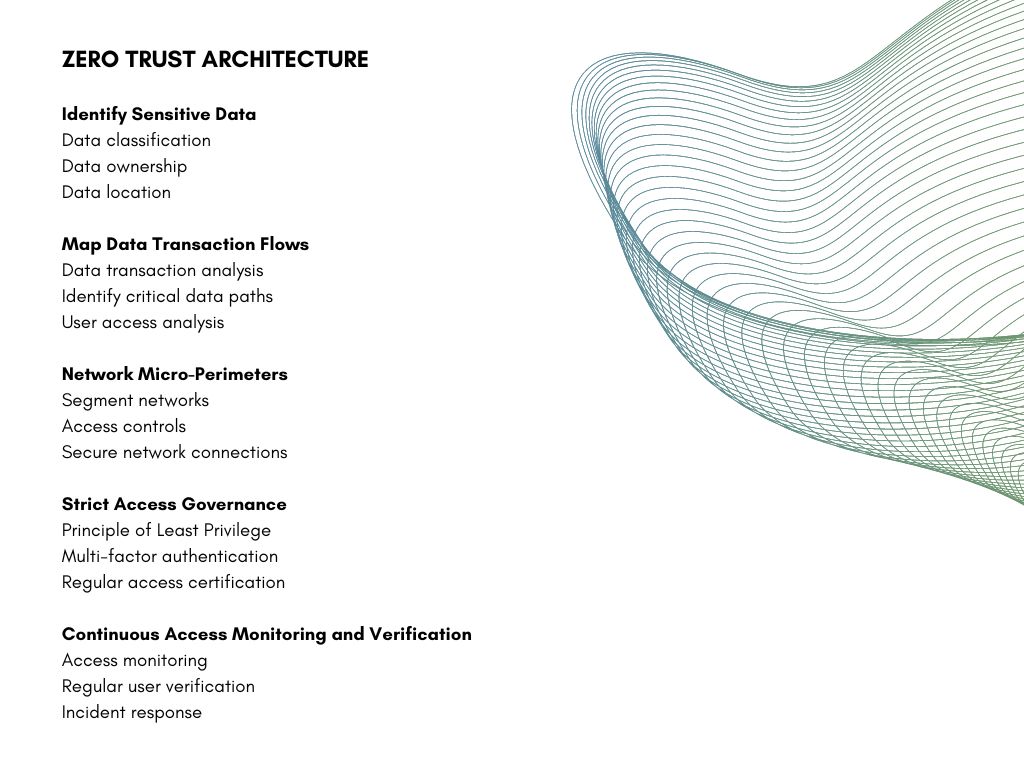
How to Build a Zero Trust Identity Architecture
The Zero Trust Architecture (ZTA) framework implements a structured approach to designing and implementing security controls and technologies within your organization's network infrastructure. ZTA aims to protect critical assets by assuming no user or device can be trusted by default.
Key components of Zero Trust Architecture include:
Identity and access management: Strong authentication mechanisms, such as multi-factor authentication (MFA), are used to verify the identity of your users and devices. Access controls are based on the principle of least privilege, ensuring that users and devices only have access to the resources they need to perform their job role.
Continuous monitoring: Real-time monitoring of user behavior analysis is essential in a Zero Trust Architecture. Anomaly detection, analytics, and threat intelligence are used to identify possible security incidents or policy violations quickly.
Security and control automation: Advanced security control solutions identify and respond to threats more effectively, while automation and orchestration help to streamline your security processes and reduce response times.
Zero Trust Architecture is designed to be flexible, scalable, and adaptable to evolving threats and technologies. It emphasizes a holistic and layered approach to security, focusing on continuous monitoring, user-centric access controls, and risk-based decision-making. By implementing a Zero Trust Architecture, your organization can enhance security and protect critical assets from novel threats and unauthorized access.
Zero Trust Use Cases
Zero Trust Architecture (ZTA) can be applied to various use cases across industries and organizations. Common use cases for a Zero Trust Architecture include:
Privileged access management: Zero Trust principles are particularly valuable in managing and securing your privileged accounts with elevated access privileges. By implementing Zero Trust, your organization can enforce strong authentication, least privilege access, and continuous monitoring of your privileged users and accounts.
Remote workforce: With the increasing prevalence of remote work, Zero Trust provides a strong security foundation. It ensures that remote users accessing your digital resources outside the traditional network perimeter are authenticated, authorized, and granted secure access based on their identities.
Cloud computing: As your organization migrates its infrastructure and applications to cloud environments, Zero Trust helps you secure access to cloud resources. Only authorized users and devices can connect to your cloud services, regardless of location or network connection.
Third-party access: Your organization likely collaborates with external vendors, partners, and contractors who require access to internal resources. Zero Trust helps you establish secure connections with third parties and ensures they are granted appropriate access privileges based on their identities and the specific resources they need to perform their job role.
Bring Your Own Device (BYOD): Many organizations allow employees to use personal devices. Zero Trust enforces strong authentication, device posture checks, and access controls to mitigate the security risks associated with BYOD.
Internet of Things (IoT): IoT devices introduce new security challenges due to their large-scale deployment and potential vulnerabilities. Zero Trust can help you secure IoT devices by authenticating them, monitoring their behavior, and controlling their access to your digital resources.
These use cases highlight how Zero Trust can be applied to secure various aspects of modern IT environments. Your organization can strengthen its security posture by adopting a Zero Trust strategy, protecting sensitive data, and mitigating the risks associated with evolving cyber threats and complex network landscapes.
Benefits of a Zero Trust Strategy
Implementing a Zero Trust strategy offers several benefits for organizations looking to enhance their security posture and protect sensitive assets, including:
Improved security: Zero Trust mitigates the risk of unauthorized access and reduces your attack surface by assuming that no user or device is inherently trustworthy. This approach focuses on verifying identities, enforcing strict access controls, continuously monitoring user behavior, and enhancing network security.
Increased visibility and control: Zero Trust architectures give your organization greater visibility into user attributes, enabling proactive threat detection and response.
Support for remote work and cloud environments: Zero Trust provides a solid framework for securing remote access and cloud resources with the rise of remote work and cloud computing. It enables your organization to enforce strong authentication, access controls, and secure connections regardless of the user's location or network connection.
Compliance and regulatory alignment: Zero Trust aligns with many compliance requirements and regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). Implementing a Zero Trust strategy can help your organization meet its regulatory obligations and demonstrate a commitment to data protection.
Adaptability to evolving threats: Zero Trust is designed to be adaptable and scalable, allowing organizations to respond to emerging security threats and technologies. The framework can accommodate new devices, applications, and network environments, ensuring ongoing protection against evolving cyber risks.
Simplified security architecture: Zero Trust can simplify your security architecture by consolidating various security controls and technologies into a coherent and unified framework. This consolidation improves your security operations' manageability and efficiency and reduces complexity for your security teams.
In today's rapidly evolving threat landscape, traditional security models that rely on perimeter defenses and inherent trust are no longer sufficient. This is where Zero Trust emerges as a powerful strategy to combat cyber threats and protect your critical assets. Your organization can use a Zero Trust approach to enhance its security posture, minimize the attack surface, and mitigate the risks associated with unauthorized access and data breaches.
Furthermore, Zero Trust aligns with the requirements of remote work, cloud computing, and the proliferation of IoT devices, providing a solid foundation for securing these modern IT environments. It also supports compliance with regulatory standards, ensuring your organization meets data protection and privacy obligations.
Want to learn more about how SafePaaS can enhance your Zero Trust security strategy?
Recommended Resources

Control Third-party Access Risk
You're not alone if your organization frequently provides vendors, suppliers, contractors, and non-staff members access to internal networks and systems. Organizations are increasingly dependent on third-party vendors to deliver business-critical products and services. However, your organization takes on enormous risks every time you provide access to a third party

Data Breaches are the New Normal
Learn how to detect, remediate and prevent data breaches in Oracle.

Unified Privileged Access Management
Many organizations use a fragmented approach to PAM using various tools from different vendors to address their needs. SafePaaS strengthens your security posture by simplifying PAM and unifying your tech stack into a single platform where organizations can manage and control all types of privileged authorizations for ALL identities using policy-based just-in-time access.

