Access Orchestration for enterprise-wide Access Management

How ERP customers can achieve reliable Access Orchestration
According to Gartner, “Access management has become the source of trust for identity-first security.” (Gartner 2020 security and IAM survey) Expanded reliance on identities for on-the-go access calls for solutions to be more reliable and simpler to embrace.
The current solution offerings from Identity Governance and Administration (IGA), and Privileged Access Management (PAM) vendors are unable to provide effective application access controls because the user entitlements defined in these systems are based on high-level abstract roles that are unreliable at assessing risks in complex enterprise application security privileges. As a result, 31% of the IGA customers are replacing their IGA solutions where the incumbent solution does not meet the requirement - according to the Gartner 2020 security and IAM survey.
SafePaaS Spring 2022 release includes enhanced IGA capabilities and Identity Orchestration for incumbent IGA systems to offer deeper capabilities for segregation of duties in Enterprise Access Monitor™, identity certifications in Enterprise Access Certification Manager™, and access request management in Enterprise iAccess™. These simplified, targeted solutions require less expertise to deploy or manage than the legacy IGA systems.
The following diagram illustrates how SafePaaS can be deployed to ensure a reliable Access Orchestration solution for enterprise-wide Access Management:
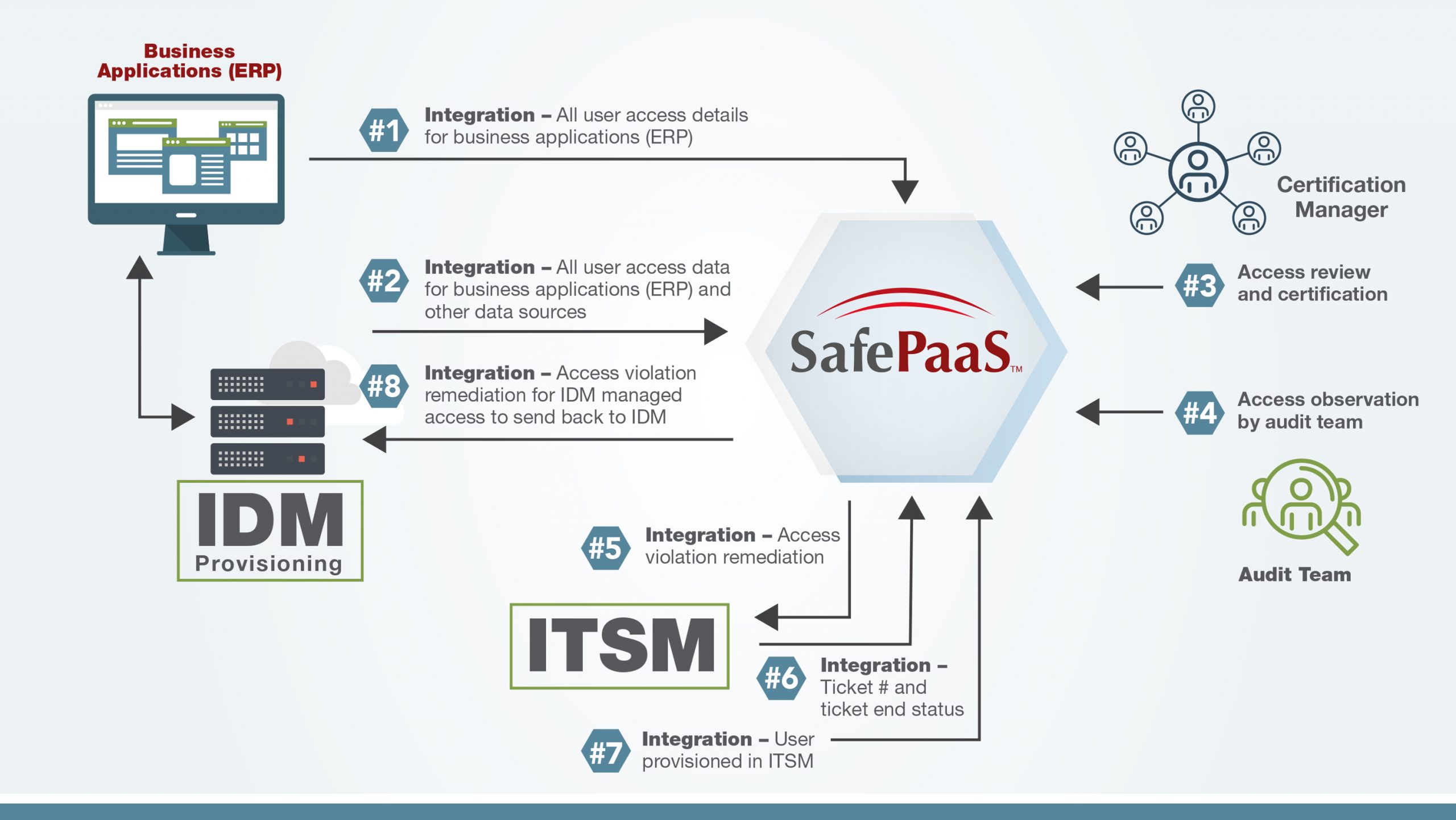
SafePaaS Enterprise Access Management solution can ensure reliable access orchestration by seamlessly integrating ERP applications with IAM, IGA, and ITSM systems as follows:
1. Maintain all User Access Details (Security Model) for any App, DB, Server, or Cloud using no-code configurable security objects that connect to data sources using industry-standard API services protocols such as REST/SOAP/JDBC and formats such as XML / JSON and CSV.
2. Monitor all User Access Requests from provisioning systems for enterprise-wide systems. The requests can be parsed by applications, business units, market segments, or any other attribute required to control access risks and cross-reference ERP roles with roles catalogs in the provisioning systems such as IGA, IAM, and ITSM.
3. Manage enterprise-wide Access Review and Certification for any system – On-Premise, Cloud, database, or server. Assign certifiers using the existing manager hierarchy or manual assignments within SafePaaS. Setup customized communication templates based on certification campaign objectives. Auto terminate uncertified users past the control survey to ensure full compliance with integration to ITSM systems such as ServiceNow.
4. Provide single-source enterprise-wide access controls effectiveness evidence for audit teams including Certification Detail with Service Ticket status, and association of abstract roles with related ERP entitlements.
5. Integrated Access Violation Remediation with ITSM system using API services to post tickets and request ticket completion status at user-defined schedules.
6. Monitor Access Request Ticket status using API services to monitor progress on tickets posted to the ITMS system.
7. Maintain audit records of all Access Requests in ITSM to reconcile against the request from other provisioning sources such as IAM, IGA, Email, and Direct updates in business applications to detect and remediate any policy violations
8. Post Access Change/Termination Requests in IDM/IGA and verify access request status. Maintain Audit Report enterprise change request. Detect risks of provisioned requests outside the IGA process.

