Safeguarding the Enterprise: Why you should Prioritize API Security


Safeguarding the Digitally Connected Enterprise:
Why you should prioritize API Security
Enterprise today is digital and interconnected. Application Programming Interfaces (APIs) are crucial in supporting that digital connectivity. APIs act as bridges allowing different systems, applications, and services to communicate and share information smoothly. But, this connectivity brings risks if APIs are not properly secured. To protect your data and operations from threats, you must secure your APIs.
In recent years, API-related breaches have made headlines, revealing the devastating consequences of overlooking API security. From exposing sensitive customer data to disrupting critical business operations, the implications of a compromised API can be far-reaching, leaving your organization vulnerable to financial losses and irreparable reputational damage. Because in this interconnected digital era, fortifying your APIs isn't just a best practice; it's a vital necessity for sustainability.
Organizations must build an API security fortress that ensures data protection, compliance, and uninterrupted business operations.
What are APIs, and why are they important
APIs are sets of rules and protocols that allow different software applications to communicate and interact with each other, for example, cloud services, IoT devices, and banking systems. APIs are also a fundamental part of software development, enabling various services and applications to exchange data and functionality. And API security refers to the safeguards your organization puts in place to protect the integrity of those APIs.
Ensuring API security is crucial because APIs act as gateways between different systems, making them potential entry points for cyber attacks. If API security is weak or compromised, it can lead to security risks, such as unauthorized access, data breaches, and service disruptions.
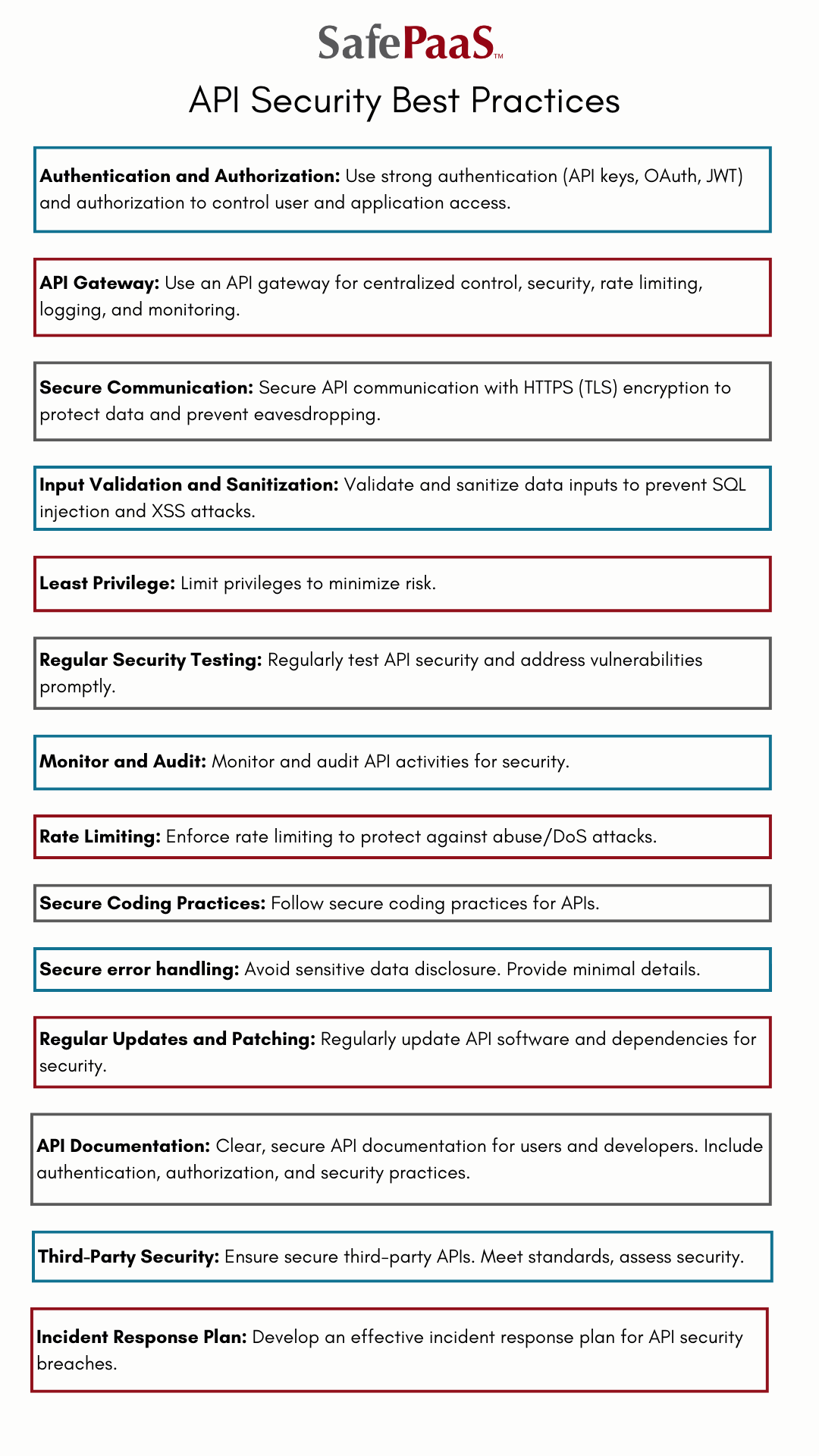
Best practices to secure your APIs
Here are the essential measures that you can take to secure your APIs effectively:
Authentication and authorization: Implement robust authentication mechanisms such as API keys, OAuth, or JSON Web Tokens to verify the identity of users and applications accessing the API. Use authorization mechanisms to control what actions or data each authenticated user or application can access.
API gateway: Utilize an API gateway as a central point of control for your API traffic. The gateway can enforce security policies, perform rate limiting, and provide logging and monitoring capabilities.
Secure communication: Encrypt your API communications using HTTPS to ensure data confidentiality and protect against eavesdropping and man-in-the-middle attacks.
Input validation and sanitization: Validate and sanitize all data inputs to prevent common vulnerabilities like SQL injection and cross-site scripting attacks.
Least privilege: Follow the principle of least privilege by providing only the necessary permissions to your APIs. Limit access to sensitive data and functionalities, ensuring each user or application has the minimum required privileges necessary to perform the required task.
Regular security testing: Conduct regular security assessments and penetration testing on your APIs to identify vulnerabilities and weaknesses. Address and remediate any weaknesses quickly.
Monitor and audit: Implement comprehensive logging and monitoring mechanisms for your API activities. Monitor for suspicious behavior, abnormal traffic patterns, and potential security incidents.
Rate limiting: Enforce rate limiting to prevent abuse or overload of your APIs and protect against Denial of Service attacks.
Secure coding practices: Follow secure coding practices when developing your APIs, such as input validation, output encoding, and avoiding hardcoding sensitive information.
Secure error handling: Ensure your error messages don't disclose sensitive information and provide minimal details to users and developers.
Regular updates and patching: Keep your API software and dependencies up to date with the latest security patches to mitigate vulnerabilities.
API documentation: Provide clear and secure API documentation to your users and developers, including information on authentication, authorization, and best security practices.
Third-party security: If you integrate with third-party APIs, ensure they meet security standards and undergo a thorough security assessment.
Incident response plan: Develop a well-defined incident response plan to handle potential security breaches and respond swiftly and effectively if an API security incident occurs.
API security is an ongoing process, but by following these steps and adopting a proactive approach to API security, your organization can significantly reduce the risk of security breaches and protect critical data and operations from potential threats.
API security and Cloud API security: What's the difference?
API security:
API security refers to the practices and measures taken to protect APIs regardless of where they are hosted or deployed. For example, APIs can exist across your various environments, including web, mobile, cloud, and more.
Cloud API security:
Cloud API security, on the other hand, specifically focuses on securing APIs used within cloud computing environments. Cloud APIs are interfaces that allow applications and services to interact with your cloud platforms and services, enabling functionalities like data storage, computation, and networking.
The main concern of cloud API security is to protect your APIs from unauthorized access, data breaches, and other vulnerabilities within your cloud ecosystem. This involves employing authentication and access control mechanisms to ensure that only authorized users and applications can access your cloud resources through the APIs.
How Identity Governance and Administration can be your strongest ally in API security
An Identity Governance and Administration (IGA) platform can be a pivotal ally in securing your APIs. With its robust capabilities in managing user identities, access controls, and authentication, an IGA platform is crucial in fortifying your API security and safeguarding sensitive data.
Identity management: IGA platforms provide centralized user identity and access management, enabling your organization to control and manage access to APIs. By ensuring that only authorized users or applications have access to specific APIs, IGA platforms prevent unauthorized access and potential security breaches.
Policy-Based Access Control (PBAC): IGA platforms that support PBAC allow your organization to define policies and assign appropriate permissions to users. This ensures that users or applications only have access to the APIs and resources relevant to their privileges, reducing your attack surface and minimizing potential security risks.
Automated provisioning and de-provisioning: IGA platforms facilitate automated provisioning and de-provisioning of your user accounts, including API access. When API privileges and identities change, the IGA platform can automatically grant or revoke API access, reducing the risk of orphaned accounts and unauthorized access.
Access certification and reviews: IGA platforms enable regular access certification and reviews, ensuring that API access permissions are up-to-date and aligned with business requirements. This helps you identify and remediate unauthorized or unnecessary access, bolstering API security.
Audit and compliance: IGA platforms maintain detailed audit logs of identity activities, including API access and usage. This enables your organization to monitor and track API-related activities, aiding in compliance efforts and investigations in case of security incidents.
Multi-Factor Authentication (MFA): Many IGA platforms support MFA, adding an extra layer of security to API access. By requiring your users to provide multiple forms of authentication, such as a password and a one-time token, the IGA platform reduces the risk of unauthorized access.
Integration with API gateways: IGA platforms can integrate with API gateways, allowing your organization to enforce access policies and security measures at the API gateway level. This centralizes security controls, making it easier to manage and monitor API access.
By leveraging a policy-based IGA platform's capabilities, your organization can strengthen its API security, reduce the risk of data breaches, and ensure that access to APIs is well-managed and aligned with business needs and compliance requirements.
APIs are critical in facilitating seamless communication between different systems and services. However, this connectivity also brings security risks that your organization must address to safeguard its data and operations.
Neglecting API security can lead to devastating consequences, such as exposing sensitive data and disrupting critical business operations. Adopting an IGA platform can be a powerful ally in API security by providing centralized user identity management, policy-based access control, automated provisioning, and auditing capabilities, strengthening your API security.
API security is an ongoing process, but by taking proactive steps and leveraging the right solution, your organization can significantly reduce the risk of security breaches and protect critical data and operations from potential threats. Prioritizing API security is a crucial investment in the future of your digitally connected enterprise.

