Best Practices Access Certification


Best Practices Access Certification
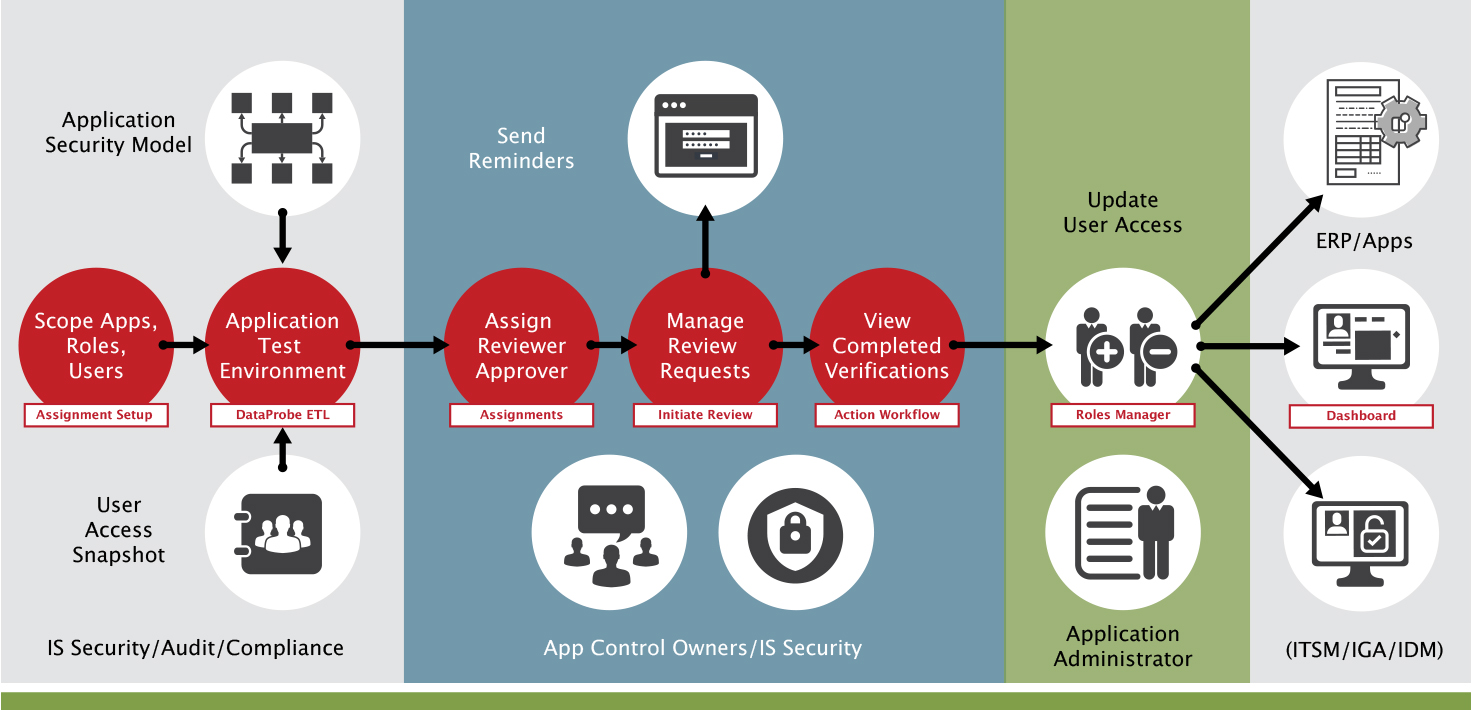
SafePaaS provides a complete platform for access governance. The diagram below illustrates best practices for access certification.
You can see how in the first swim lane, you scope your applications, roles, and users. Those are set up within SafePaaS and provide visibility into what roles users are assigned, the specific process owner, role, and responsibilities. That is the baseline for the certification process.
Data from your ERP is brought in through "snapshots." Then SafePaaS brings in the application security model to provide users that don't have access to your ERP a complete understanding of what they will be providing access to.
In the blue swim lane, reviewers and approvers are assigned to different parts of the application. You can set it up where you may have super user status -usually somebody in the IT department. You want to ensure that users have access and are monitored correctly. Once you initiate those assignments, you run the analysis. From there, the business process owners are notified by e-mail containing a hyperlink that users have access to the different parts of the application that they're responsible for. They can go in and decide to approve or terminate access.
Then as you go through that process, you can upload that data into SafePaaS, which is done automatically until the actual certification process closes. Once it's closed, you can no longer update it. Once that access is updated, you can run it into SafePaaS, depending on whether it's approved or terminated. SafePaaS will also kick out a service ticket and remediate that particular access.
Features:
Intuitive Review and Certification
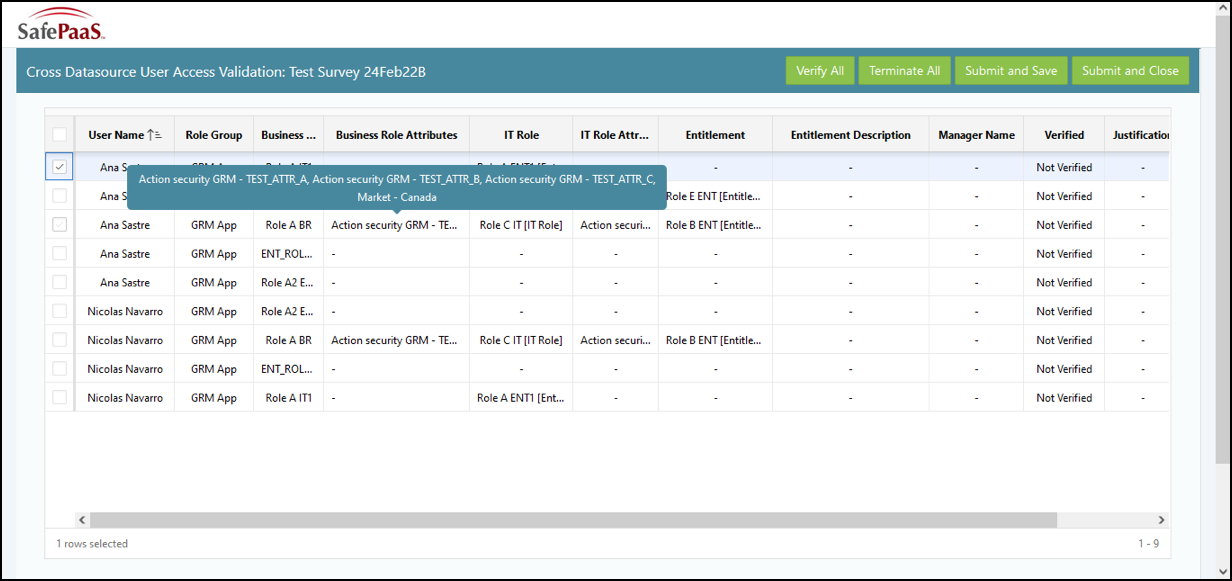
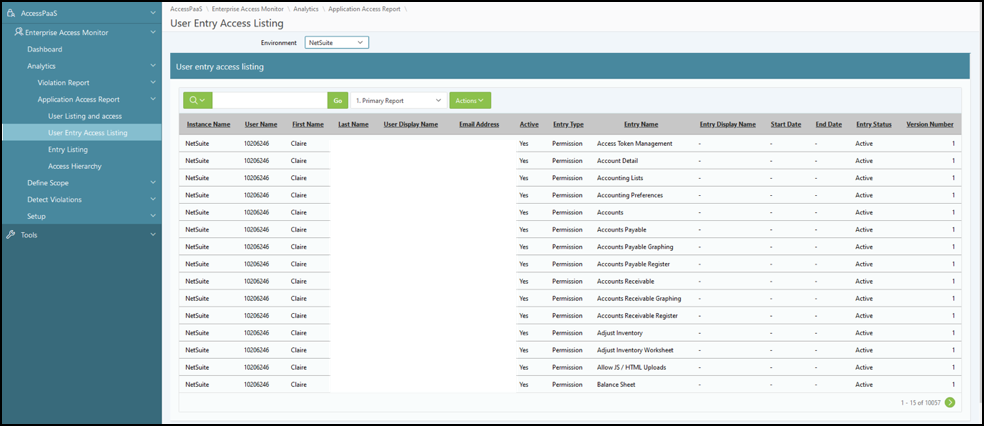
The screenshot below illustrates cross-linked data sources. Cross-links have different applications or data sources, and users are analyzed between the various data sources.
Suppose you have a user with access to the ERP and want to see other users who have access to the database. You can create a cross-link relationship between those two data sources and generate an access certification based on those data sources to identify users that have access to both data sources. Then the process owner can decide whether they want to approve or terminate the user’s access.
Consolidated Controls Management and Administration
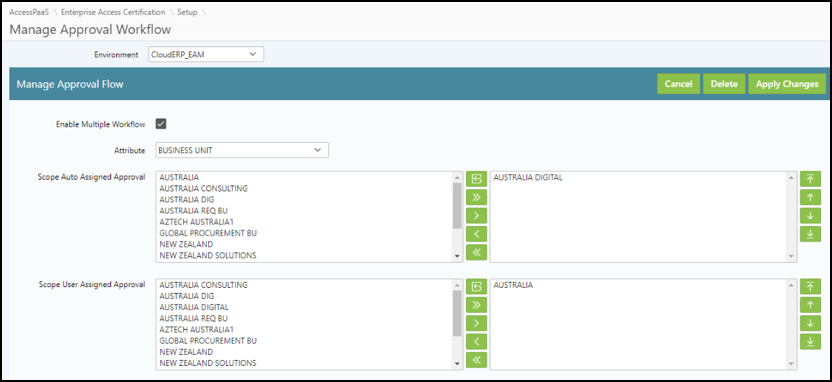
When it comes to workflow, you can define workflow based on attributes or groups. Instead of assigning an individual, you can assign it to a group. In this example, the Business unit is the group used by individuals within the business hierarchy. The SafePaaS workflow is both flexible and configurable.
Centralized Certification management, based on risk groups, markets, business unit any other user defined attributes:
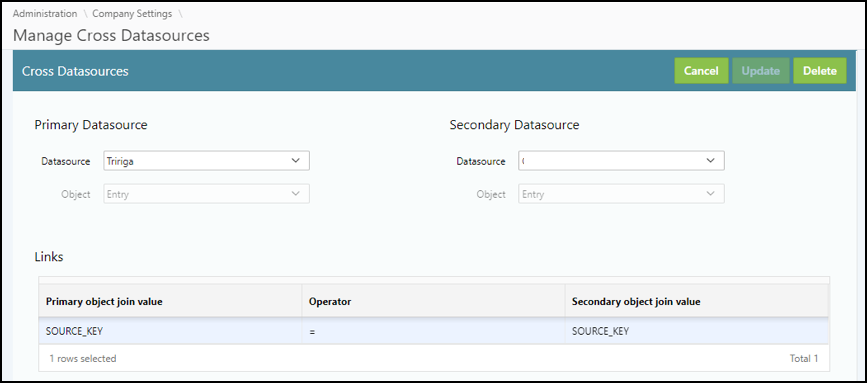
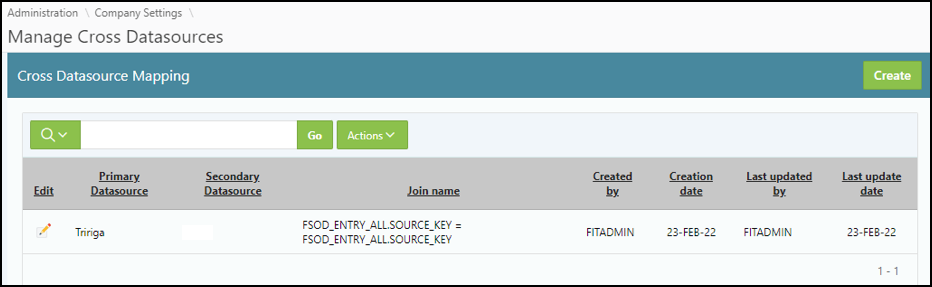
This screenshot represents the cross-data mapping of different data sources. This is an excellent example of Tririga and SailPoint. You create that relationship, and then when the certification process is initiated it will identify users in those data sources and bring them to the process owners for review.
Closed-loop workflows with notifications
The notification is processed through e-mail. An e-mail is sent to the process owners. At that point, you can use the hyperlink in the email, drill down into SafePaaS, or the certification review. The process owner can decide to set the level of access for each user.
As you continue to update the application, all the reports are kept current in SafePaaS. Depending on the date you set to close the survey, it will no longer allow you to update or automatically close it.
Seamless Integration with all data sources on-premise and cloud protocol supported
SafePaaS seamlessly integrates all data sources, whether on-premise or in the Cloud. We provide technology to allow you to bring that data into SafePaaS for analysis and its subsequent certification of users across your organization.
Intelligent, Rule Based Fine-Grained User Security Risk Discovery
SafePaaS can also track your super users for privileged access management requirements and what super-users have access to in the ERP. If you provide users with increased access for any reason, those users and what they touched will be tracked in SafePaaS.
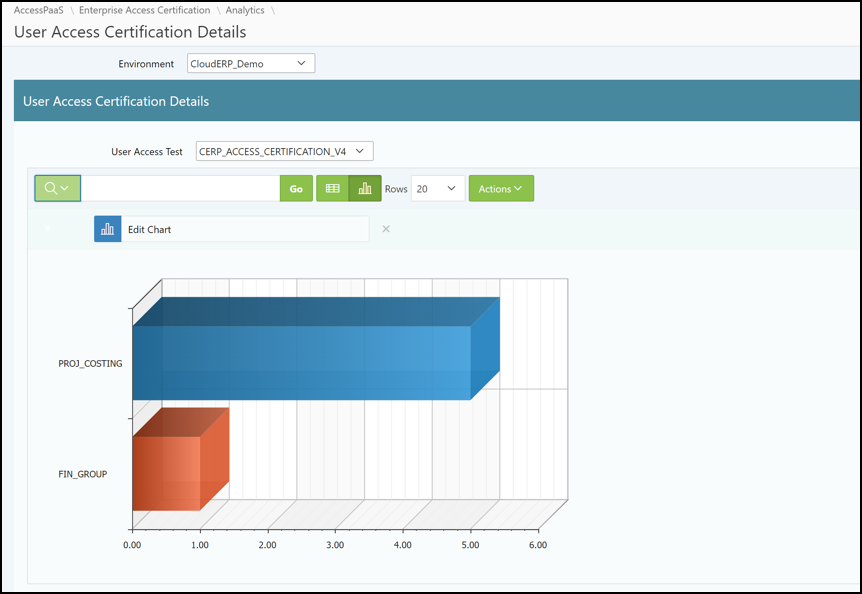
Monitoring dashboards
SafePaaS also has significant reporting capabilities. We have a simple graph generated by the application, and you can configure it specifically to your needs.
Recommended Reading

Enterprise Access Certification Manager
Automate User Access Review and Certification to control access across all Cloud Infrastructure, Operating Systems, Databases. ITSM and Applications.

Achieve Access Orchestration
Current solution offerings from Identity Governance and Administration (IGA), and Privileged Access Management (PAM) vendors are unable to provide effective application access controls because the user entitlements defined in these systems are based on high-level abstract roles that are unreliable at assessing risks in complex enterprise application security privileges.

Streamline Fragmented Access
The cloud is making it more cost-effective to roll out applications because of the ease of connecting to the cloud. However, having so many applications is causing a problem of fragmented access.

