
SafePost Quarterly Newsletter
We start this year with gratitude to our customers worldwide that have collectively analyzed over 5.7 million ERP application users and detected over 445 million unique risk incidents to protect their business and comply with policies – making SafePaaS the single most utilized cloud platform for detecting and controlling access risk in enterprise applications. Our customers can take advantage of the scalable platform to benchmark access risks and make faster, better decisions to control, remediate, and mitigate risk in critical business applications.
With significant enterprise customer wins, new hires, and growing strategic alliances, our business grew 51% as we introduced 494 new releases to continue our mission of making the platform more reliable, secure, and useful for our customers in detecting hidden system risks to seize new opportunities and achieve performance goals. As organizations adopt single-source least privilege access models with self-service automated policy-based Identity Governance Administration
(IGA) and risk-aware access management solutions to secure business- critical applications such as ERP systems, SafePaaS will continue to innovate in 2022 enabling our customers to protect enterprise business applications against emerging cyber threats and ensure sustainable compliance with access policies.
Following are just some of the most popular enhancements on our platform available for
deployment in 2022:
Automate User Access Certification for enterprise-wide applications and Infrastructure
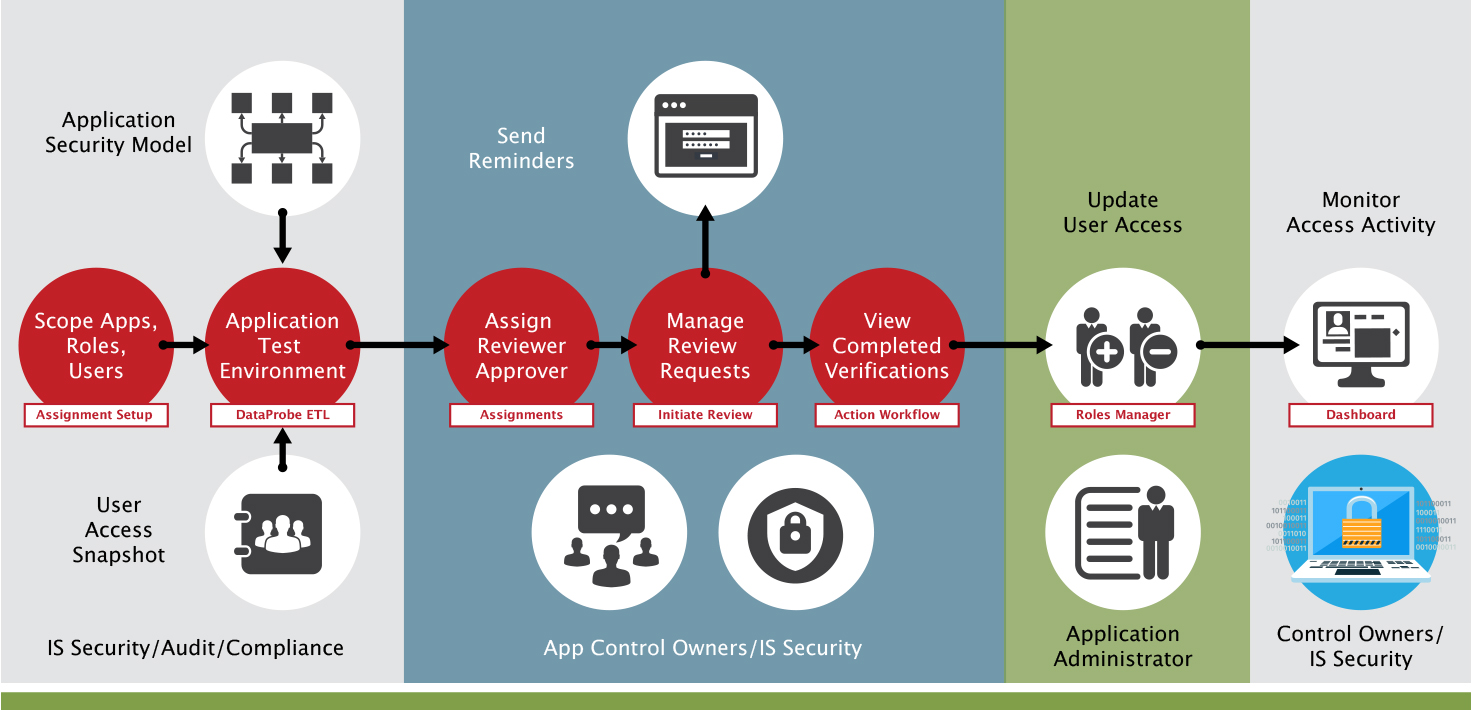
Your business is more dynamic than ever – employees come and go, they change roles, they move departments. Roles are no longer static – that’s why automating access certification is more important than ever to secure your business-critical systems.
SafePaaS Enterprise Access Certification Manager - EACM™
EACM™ makes it easy to manage and control access and keep the auditors at bay. Automating the process not only replaces a manual time-consuming task but ensures compliance. Automating access reviews can save you hundreds of hours on manual reviews of access role assignments and privileges within your business-critical applications.
Our clients are deploying our access review solution across all business-critical applications with full integration with IGA systems such as Okta, SailPoint as well as ITSM systems such as ServiceNow allowing them to streamline certification globally using a cost-effective, scalable solution.
Extend Access Controls to all your business-critical applications beyond your ERP System for Complete Coverage
Did you know that many SafePaaS customers use our platform as a hub for all access controls to ensure access governance across the enterprise? Whether that be popular ERP systems such as Oracle Cloud ERP, E-Business Suite, PeopleSoft, JD Edwards, NetSuite, or Business Process solutions such as Salesforce for CRM, Workday for HCM or Coupa for Procurement, Hyperion/EPM for Financial Reporting as well as many industry-specific applications, SafePaaS provides the capabilities to integrate with your favorite applications ensuring audit, security and risk is controlled enterprise-wide.
As both cyber and insider threats continue to pose a real danger to organizations, it becomes paramount to have complete visibility into security across the entire enterprise. Being able to seamlessly integrate with any application will allow SafePaaS customers to have a controlled, real-time view of user access across the business. SafePaaS can certify at the granular level needed for assurance of any enterprise role no matter where the role exists, creating cross-reference between roles for a more streamlined view of risk.
Control User Access Request Management Across the Enterprise
Digitalization and the constant evolution of business and IT landscapes together with the increased adoption of hybrid work models, hundreds of cloud applications along with legacy on-premise applications has materially increased the risks in user access request management. Organizations with complex enterprise systems, require Identity Governance
and Administration solutions that ensure policy-based access controls to ensure compliance with access policies such as Segregation of Duties and Restrictive Access.
iAccess Enterprise™ provides advanced policy-based access controls allowing organizations to control who is given access to what set of data, at what time under what policies. Policy-based access controls adapt efficiently in real-time to control and manage access dynamically across all your applications.
Detect ERP Misconfigurations, suspicious transactions, and unauthorized Master Data Changes in Cloud Applications
Can you confidently say that you know all the user activities in your ERP applications that may lead to financial misstatements, waste, bottlenecks, or fraud?
Today more than ever, organizations need to transform risk management practices from manual controls to automated fine-grained controls that monitor business activities enabled by enterprise applications.
Management is suffering from “Audit Fatigue” as regulators around the world impose stringent compliance requirements to ensure transparency and protect stakeholders.
Manual controls are ineffective without timely visibility into control violations that occur in daily business activities within enterprise applications such as changes to supplier bank accounts, customer credit limits, three-way match, as well as transaction control failures e.g. split purchase orders and duplicate payments.
The bottom line is that if any of the key controls in your enterprise application fail to operate, there will be an impact on the business—usually in the form of a surprise.
The latest enhancements to MonitorPaaS™ enable you to control business process risks across the enterprise, as your business process extends beyond a single application. MonitorPaaS™ delivers actionable insight into your business processes for a timely response to events based on the risk tolerance and treatment guidelines established by management and mandated by regulators.
You can continuously monitor business activities within your enterprise applications with instant access to the largest catalog of automated application monitors covering business objects for major processes such as Procure-to-Pay, Order-to-Cash, Hire-to-Retire, Design-to-Ship, and Financial Record-to-Report.
Cross-application Advanced Access Risk Analytics
As organizations adopt best-of-breed applications, cross-application capabilities become necessary for increased visibility into risk. Organizations require real-time deep analytics for better-informed business decisions and maximum performance. Advanced analytics show organizations where they need to focus in real-time for timely remediation.

