Top 5 strategies SoD Oracle ERP Cloud


Top 5 Strategies to remediate segregation of duties in Oracle ERP Cloud
Unaddressed SoD conflicts pose risks to financial statements, operational activities, and the alignment of roles and responsibilities. In recent years, auditors have increased their focus on the remediation and mitigation of SoD conflicts. However, many organizations struggle with how to address remediation issues.
Remediation is crucial in addressing access control incidents where policies have determined the existence of a violation. Remediation involves multiple participants from the business, audit, and I.T. to choose the appropriate corrective action.
The following are some of the possible corrective actions you can use to remediate your SoD conflicts:
1. Define access risks
The foundation of mitigating SoD conflicts is identifying them based on the organization's risk tolerance. It is important to have a rule set that addresses financial and operational access risks yet is adaptable to organizational changes. SafePaaS AccessPaaS™ allows you to automate the identification of SoD and sensitive access risks at the most granular level in the security model to ensure completeness and accuracy.
This diagram below exemplifies the user security model access structure in Oracle ERP Cloud. The Oracle ERP Cloud security model is flexible however, given the complexity of the design, it’s essential to design and build security in the implementation phase to ensure effective segregation of duties.
Oracle ERP Cloud security is based on role-based access security. The role-based security model also called role-based access control (RBAC), restricts system access to the users. A user should not have access to perform all activities within a process, system, or information.
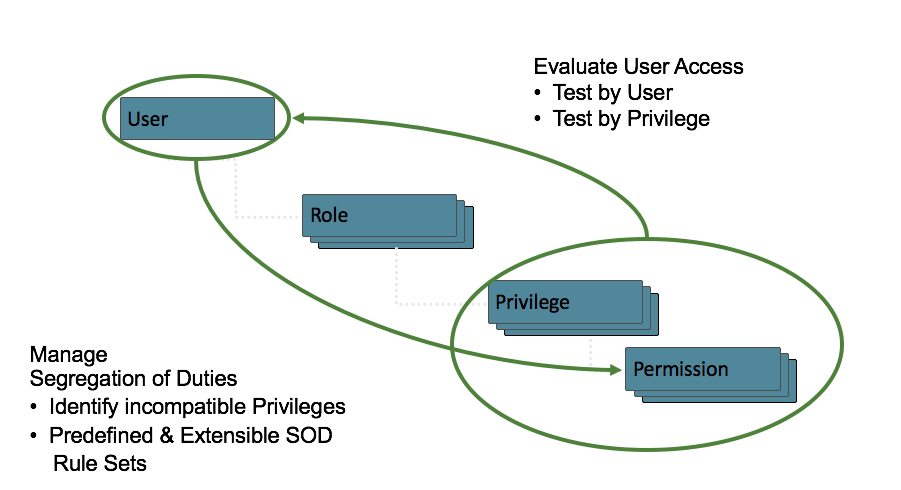
Evaluating user access is critical to minimize risk and comply with the organization’s access policies. Understanding all the roles, privileges, and other security attributes that grant users access to perform process activities is necessary. Any violations detected during this evaluation step require the security administrator to make the necessary remediation recommendations and address the known incidents.
2. Analyze user and role SoD conflicts
Your SoD solution should leverage the custom rule set and identify Segregation of Duties and sensitive access conflicts. Performing this analysis will allow the enterprise to gain visibility into the current state of access risks within the ERP system and remediate access risks. SafePaaS has easy-to-read, intuitive, drill-down, real-time dashboards. The Dashboard has several different reports to choose from to devise your remediation strategy.
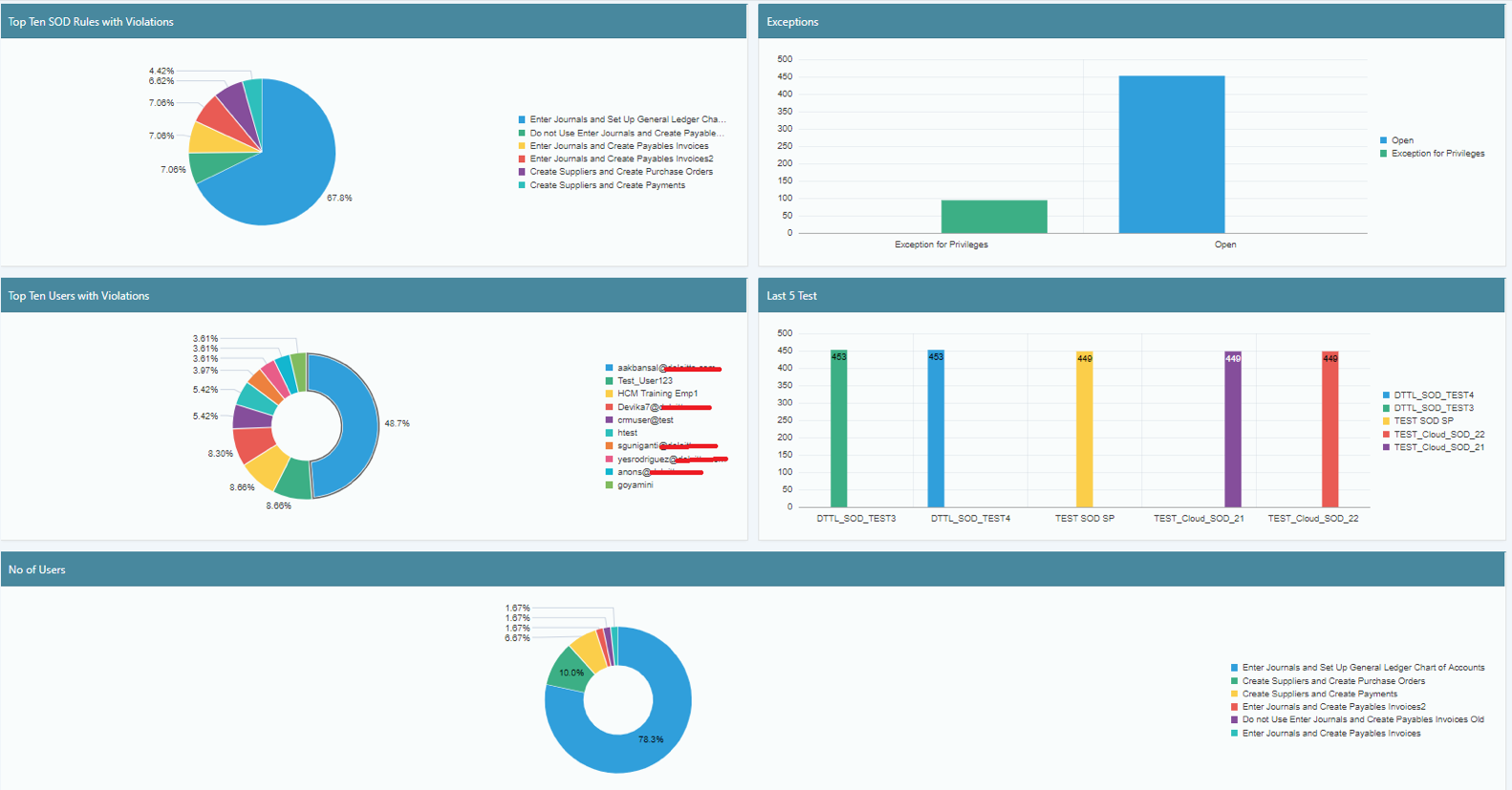
3. Remediate role and user conflicts
Using your SafePaaS SoD analytics report, you can identify the roles that contain conflicts and determine an approach to remove conflicts from roles by removing transactions or separating sensitive tasks from within roles.
4. Identify and define mitigating or compensating controls
Map available business processes and I.T. controls to the appropriate SoD and sensitive access risks. When using an existing access control is not possible, a new mitigating or compensating control must be designed and implemented. Once your controls are linked to the appropriate access risk, the user can be mapped to the proper risk and control combination.
5. Assess role design
As part of the remediation, new roles may need to be created, and existing roles may need to be modified. This can be achieved using SafePaaS Roles Manager™. Roles Manager™ is an application security design solution containing a pre-configured catalog of roles that comply with access policies for Segregation of Duty (SoD) and restrictive data access. You can use this solution to view existing role templates and design new roles by easily selecting or deselecting role configurations. Once the roles design is complete using workflows, it can be sent to pre-assigned reviewers and approvers to finalize the roles. The role preparers, reviewers, and approvers can also assess the SoD control risks before finalizing the roles. Furthermore, these can be combined into composite roles that match job responsibilities and comply with SoD policies. Our ERP Roles catalog contains Roles by ERP module and typical access requirements for those modules such as Manager, Supervisor, Clerk, Inquiry, Business Setup, and I.T. Setup.
Filter False Positives, Remove inherent false positives, and exclude local exceptions.
We consider the preceding to be best practices to remediate access risks and prevent recurrence in the future. However, most organizations must tolerate some level of access risks where the business resources are constrained. For example, in a small or remote business unit, you may have the same person enter and post journal entries. In such cases, you can deploy Continuous Controls Monitoring (CCM). CCM allows businesses to:
Identify suspicious transactions
Alert process owners when key application configurations are changed by "super users" and
Maintain an audit trail over data changes such as customer credit limits, supplier bank accounts, etc.
CCM is not covered here but should be considered as part of your compensating control strategy to manage overall access risks.
Read more about Continuous Controls Monitoring HERE

