The policy-based identity governance guidebook


The Policy-based Identity Governance Guidebook
Digital technologies are fundamentally reshaping how people work. Ever-changing application and infrastructure architectures require constant evolution to meet the challenges facing companies, government agencies, and educational institutions. To meet the demands of the changing environment, Identity Governance and Administration (IGA) also needs to adapt to making digital services available everywhere without losing control.
However, many organizations grapple with IGA processes, like creating and managing roles, assigning and reviewing access entitlements, and handling access requests. The primary cause is that organizations follow the wrong approach to IGA, particularly around creating and managing roles.
What is IGA?
IGA integrates Identity Governance and Identity Administration.
Identity Governance is a framework used to gain better visibility of user identities and access controls while complying with standards and regulations.
concerns visibility, segregation of duties, role management, analytics, and reporting.
Identity Administration is part of identity management and access management (IAM). It involves creating, modifying, or deleting identities and granting privileges and entitlements based on the user's role to manage access to resources such as applications and help to protect data security.
concerns account administration, credentials administration, user and device provisioning, and managing entitlements.
IGA solutions allow organizations to control digital identities and access privileges across numerous systems for multiple user types (employees, partners, and machines) to ensure appropriate access to resources across IT environments and compliance with government regulations.
Gartner defines IGA solutions as systems that "aggregate, correlate and orchestrate disparate identity and access rights data distributed throughout an organization's IT ecosystem."
The capabilities of an IGA solution that meets the needs of a typical organization are:
Access certification
Segregation of duty
Workflow orchestration
Entitlement management
Support for access requests
Policy and role management
Identity life cycle management
Provisioning through automated APIs and service tickets
Origins of identity management - from IAM to IGA
Identity governance initially began as an offshoot of identity access management (IAM) and was developed to meet the requirements of regulatory mandates such as SOX, GDPR, and HIPAA. IGA aims to improve the visibility and manageability of identities and access privileges to control, detect, and prevent inappropriate user access.
In 2012, Gartner recognized identity governance as the fastest-growing sector of the identity management market and stated that identity governance "is replacing user administration and provisioning as the new center of gravity for IAM."
As the IGA market matured and users began to adopt identity governance and provisioning solutions, it became clear that identity governance's role, policies, and risk models were foundational to provisioning and compliance processes. Organizations also realized they needed centralized visibility of all applications and data to effectively manage identities, risk, and compliance.
Today digitization is soaring, and organizations are witnessing ever-increasing numbers of users, data, and devices across on-premises and cloud environments. Managing user identities and access to applications and data in complex IT security ecosystems is challenging. Data access control requirements are too complex to achieve using a single user attribute (their role). This is especially true in heavily regulated industries like banking, healthcare, and government, which process Personally Identifiable Information (PII). External users access systems and applications from anywhere, and sensitive data is collected on employees and customers, including social security numbers, email addresses, and banking information. And, if users have excessive access to systems, applications, or data, it increases security risks and makes the organization vulnerable to cyberattacks and data breaches.
The challenges of RBAC identity tools
Organizations with role-based access control (RBAC) tools define roles and assign entitlements based on artificially constructed roles. For example, Finance Manager or AP Clerk. While this works in small organizations, the role-based approach becomes too complex to manage when working with hundreds of applications, clouds, and databases.
The RBAC method of managing access to data and resources functions if you never reassign an employee or work with partners. But, no organization remains static, and RBAC processes become unmanageable in dynamic environments. To cope with the limitations of role-based access controls, many organizations create integrations between their HR application, Active Directory, and IAM for synchronized role creation and continuous lifecycle management of roles. However, these integrations are expensive, fragile, and challenging to maintain and ultimately don't deliver the desired outcomes.
In the context of IGA, policies are the ideal foundation because they contain the necessary details for effective access management. Policy-based IGA facilitates the organization's administration of identities and access efficiently while improving visibility into identities and access privileges. A policy-based approach can also improve compliance and ensure that users have only the appropriate access for their jobs.
Role-based tools fall short of access governance needs in the following ways:
RBAC tools can't structure access policies with fine-grained privileges in the application security model. (See the image below)
Security models are complex, and IAM tools control user access by provisioning roles from a catalog of privileges. Often these pre-set roles contain a toxic mix of privileges and do not prevent access to sensitive data, transactions, functions and other high-risk actions. PBAC IGA solutions manage user access requests for applications and data at the privilege level instead of pre-set roles containing multiple privileges.
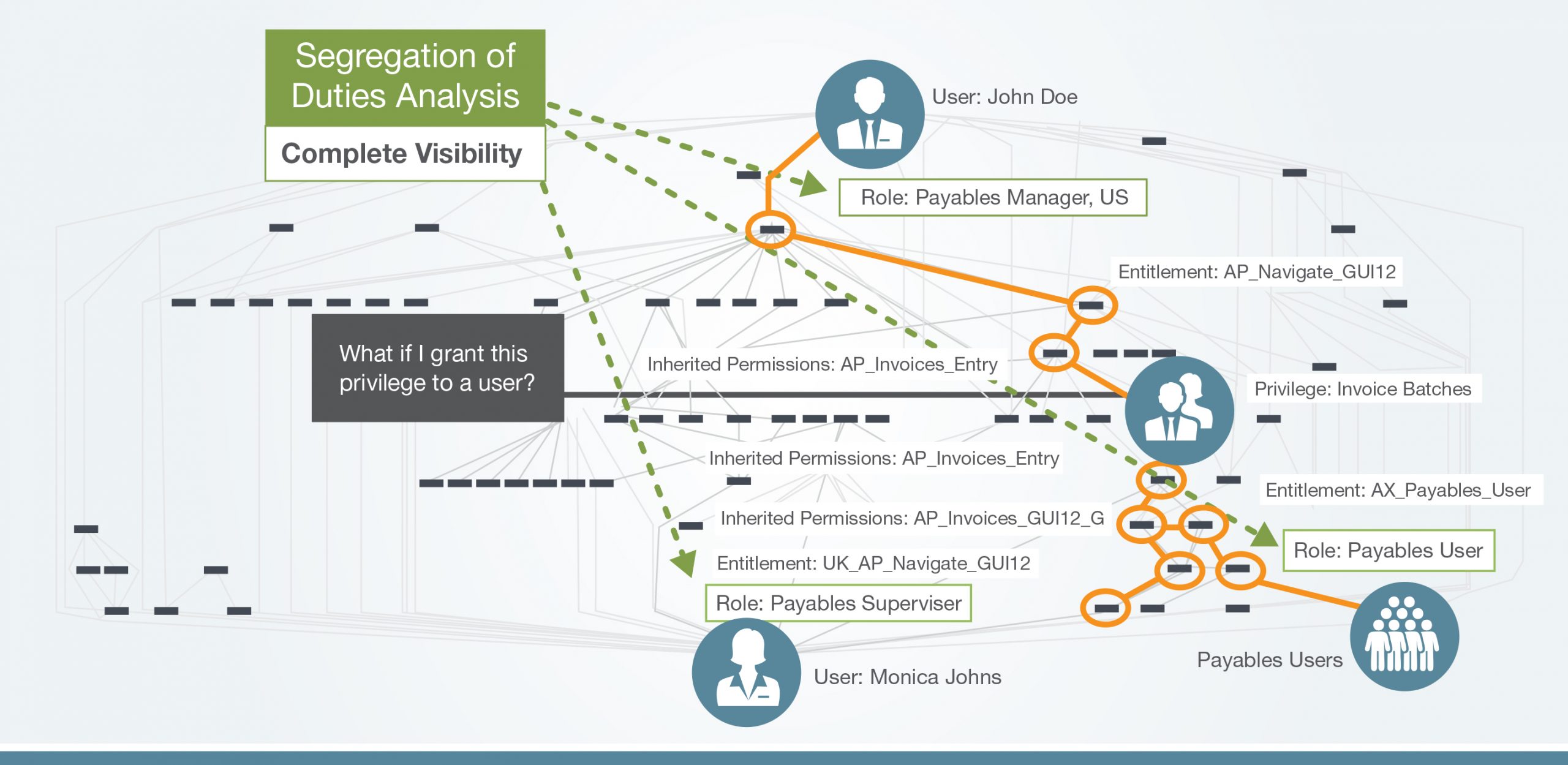
- RBAC tools are not able to assign and track Privileged Access. And once privileged access is assigned, these tools cannot monitor and document the actions made by these users.
IAM tools only identify the user and provide access to applications and services. Privileged access management controls access and the user’s actions to highly sensitive systems. In short, IAM and PAM systems identify and authorize access differently.
- IAM focuses on “birthright” access for user privileges, whereas IGA requires risk management for users with hundreds of privileges to sensitive data, transactions, and functions.
In RBAC IAM systems, birthright access is the access given to a user at the start of the user identity lifecycle. The problem with this approach is that birthright access can sometimes contain toxic privileges. For example, in a well-known ERP system, as part of your birthright, you can import supplier bank accounts into an excel file.
- Single Sign-on to applications for "birthright" users don't manage the provisioning of privileges that violate company policies, such as Segregation-of-Duties or Data Privacy.
Single Sign-on for IDM systems, like Azure AD, facilitates using a single user ID and password across all applications. Policy-based access controls help you provision and de-provision access across all applications and endpoints with fine-grained visibility into privileges and attributes. By applying policies to identities, you can achieve the visibility required to safeguard core systems.
- IAM tools do not monitor or manage user activity within applications. The ability to perform a "lookback" analysis is crucial when risk has occurred.
Auditors require a lookback analysis of the prior period's control effectiveness when risk is detected. For example, if SoD controls identify users that can violate one or more SoD policies. Once the violations are detected and remediated by changing user access assignments, the remaining unmitigated "residual" risk requires lookback analysis. IAM technologies can't do this.
- RBAC tools don't allow business processes and control owners to certify user access for access certification.
Strong cybersecurity standards require the periodic review of user access to ensure that only authorized users have access to sensitive data and systems. Any excessive access must be removed to eliminate threats.
- IAM tools do not allow security administrators to maintain role design and update entitlements to remediate inherent risks in privileges available in enterprise applications.
Many organizations manually maintain changes to privileges for critical systems. However, the manual management of roles does not allow role simulation to test for risks before making changes. Role simulation enables organizations to prevent security risks and audit findings.
Critical components of IGA for a digital enterprise
The two major components of IGA are access governance and identity lifecycle management.
Access governance refers to the policies, processes, procedures, and techniques that govern and control access to systems, data, and applications. Access governance also reduces risk by controlling privilege creep as users move throughout the organization and ensuring access is revoked when users no longer require access.
Identity lifecycle management refers to the process of managing user identities and evolving access privileges of employees during their employment, from the day they join the organization to the day they depart.
Integrating systems that enable data flow from source systems such as HR to target systems such as Active Directory is necessary to manage the identity lifecycle effectively. Automated workflows support identity lifecycle management for provisioning/de-provisioning users, access requests and approvals, and access certification.
The first step in adopting a policy-based IGA system is to define your access policies to determine who has access to what and under what circumstances. For example, User A can access documents on SharePoint but only from the office.
Benefits of policy-based IGA
1. Compliance
Compliance has never been more challenging. With so many regulations requiring data privacy, like GDPR, SOX, and HIPAA, organizations are more focused on access issues. Restricting and scrutinizing access is a crucial security measure to comply with these regulations.
IGA solutions ensure that access to sensitive information is tightly controlled. IGA solutions also enable organizations to prove they are taking action to protect data and security. Organizations can receive audit requests at any time. An effective IGA solution makes the required periodic review and access certification easy and effective, with reporting capabilities that meet applicable government and industry regulations.
2. Risk management
Data breaches and cyber attacks are on the rise. The affected organizations will spend millions on remediation efforts and dealing with the damage to their reputation.
IGA solutions are proactive and reduce the vulnerability of sensitive data by strictly limiting and guarding access to resources. IGA solutions address managing and governing access by focusing on three aspects of access.
- Employ the principle of
- Terminate orphaned accounts that are no longer in use. Bad actors target these to breach the environment.
- Monitor segregation of duty (SoD) violations. SoD ensures that single tasks are separated so no individual can complete a process alone. This creates a system of checks and balances. For example, in a financial transaction, the person who creates a supplier should not have access to pay the supplier.
3. Agility
Organizations are constantly changing, and policy-based IGA solutions can scale to meet those demands more efficiently and with less risk. Changes like promotions, transfers, and departures can quickly be made. More extensive changes, like mergers, acquisitions, and reorganizations, can also be implemented since policy-based IGA solutions provide access based on policies in addition to roles-based access. Policy-based access control (PBAC) can significantly reduce execution time in bulk actions to user accounts by automating and streamlining provisioning and approvals.
4. Reduce costs
Managing user access manually is an unsustainable burden on IT and an excellent place to start when looking to cut costs. However, there are three components of costs to consider with the manual management of identity. There is the cost of users who cannot work because they are waiting on access. There is the cost incurred by the helpdesk, which needs to manually input new users or make changes to existing user access. And lastly, there is the cost of correcting the inevitable errors that occur in all manual processes. By implementing an automated policy-based IGA solution, you are saving time and money wasted on manually managing user access.
5. Ease administration
IGA solutions are designed to make governance easier for everyone in an organization. Establishing access policies and streamlining provisioning creates an efficient onboarding process and eliminates having to wait for or stop access. Accounts are created with access based on established policies, and managers don’t have to waste time requesting access for users or worry about revoking the access of users that no longer need it.
The RBAC approach assigns access too simplistically. Policy-based IGA boosts security by enabling flexible, fine-grained identity governance, ensuring the right people receive the appropriate access to the correct data and system. With policy-based IGA, your business will operate smoothly while easily meeting compliance obligations.
Want to learn how you can benefit from a policy-based IGA platform? Why not reach out to us for a complimentary session.

