Prevent risk in Procure to Pay


How to prevent risks and streamline your procure-to-pay process
Procure-to-pay (P2P) is one of the most critical processes in every organization. An effective P2P cycle saves costs by reducing manual tasks, increasing accuracy, and improving efficiency.
However, organizations confront a range of risks when procuring goods and services. These risks can originate from several sources, including supplier financial stability, quality of goods or services, invoicing, and payments. To better understand the risks involved in the P2P process, let’s explore some common risks encountered in the process and how to mitigate them.
What is procure to pay?
Procure-to-pay is a business process spanning functions from sourcing to paying for goods and services. P2P relies on the collaboration between purchasing and the accounts payable departments to obtain goods and services for the organization. P2P aims to integrate those functions and create a smoother procurement workflow with closer control and visibility into every stage of the process.
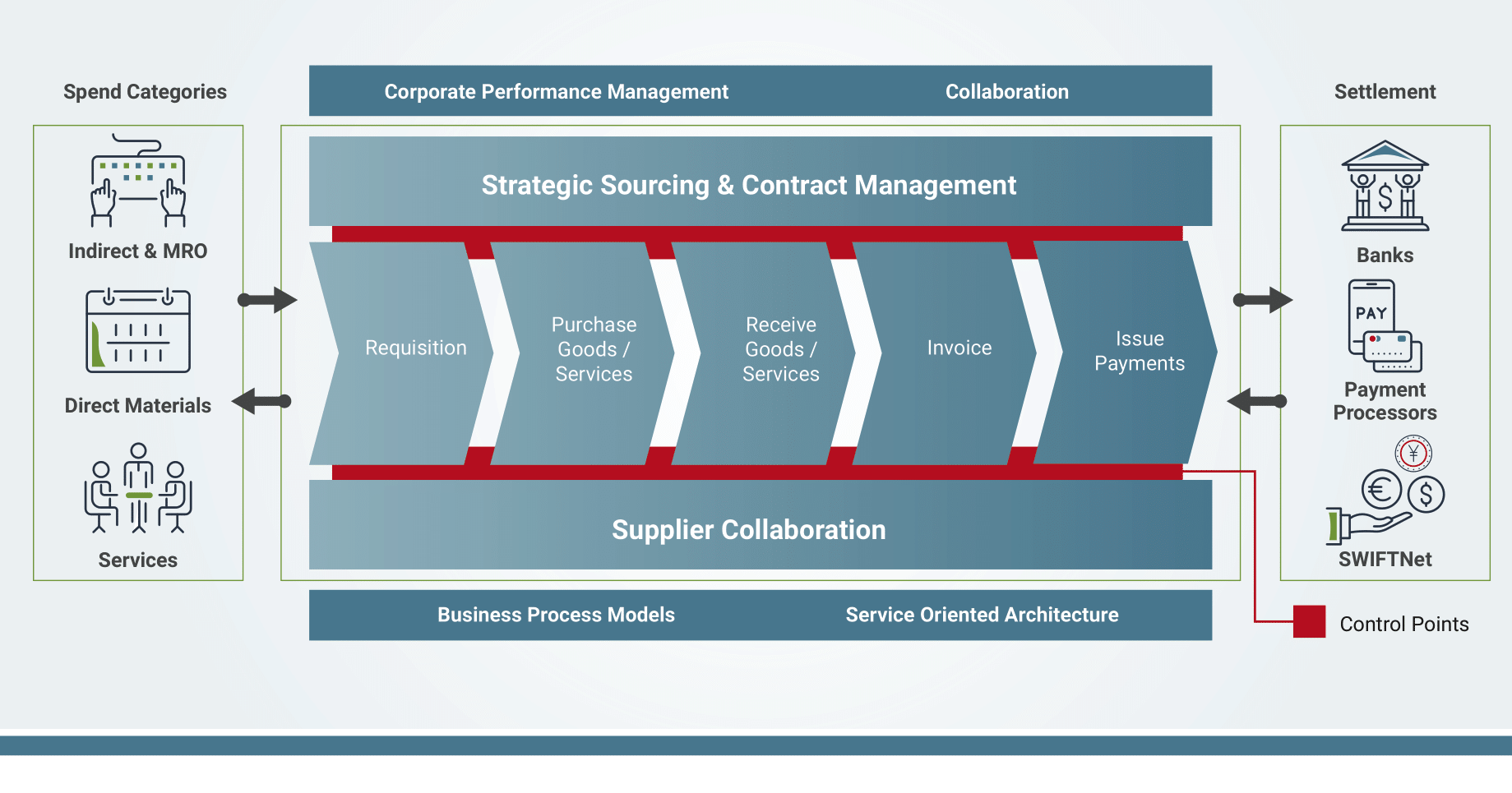
What procedures are covered in P2P?
Need - The need for a product or service is identified
Sourcing - Effective sourcing is critical to ensure that you have a solid supplier offering the best price for goods or services.
Requisition created - Request made for the goods or services.
Requisition delivered to supplier - When the requisition is approved, a purchase order is given to the supplier.
Receipt of goods - The supplier delivers the requested goods or services with a receipt.
Invoice received - The supplier's invoice is submitted, entered, and processed in the system.
Invoice processing - The invoice, PO, and the receiving documents are matched or flagged for investigation. This process is known as a three-way match.
Payment - Approved invoices are moved to accounts payable for payment and logged in the system.
Common risks in the P2P cycle
Inappropriate association between vendor and employee: An inappropriate relationship between an employee and a vendor is any relationship between an employee and a proposed vendor that might create a conflict of interest. For example, while working for a large shoe manufacturer, we discovered an employee who regularly invoiced services for electrical work provided by a family member.
Duplicate suppliers: A duplicate supplier in the P2P process is when you have a name, address, or bank account duplicated for the same company, increasing the risk of a duplicate payment being made. High transaction volumes, increased operational complexity, and the use of multiple platforms and systems make duplicate suppliers challenging to detect. While you may have strong controls, your ERP cannot distinguish between Acme Electric and Acme, Electric. And that's how duplicate data often gets into your master supplier data.
Another example of how duplicate payments can be made is in the case of unclear organizational structure. While working with a customer who had recently gone through a merger, the customer had two CIOs. Both CIOs believed it was their responsibility to pay for a hundred million dollar SAP implementation, and both CIOs paid the invoice. In the end, the customer received a reimbursement for the duplicate payment, but millions of dollars spent on time and effort to recover the duplicate payment were lost.
Trade regulations and vendor compliance: Vendor regulatory compliance risks occur when a vendor violates a law or regulation you're obligated to follow. Vendors must comply with laws, regulations, and rules that affect your organization and its internal policies. Failure to meet compliance standards can result in fines and reputational damage. For example, US trade regulations in banking and insurance are mandatory. Banks cannot open an account or transact business with you unless you are verified through OFAC. For example, a Russian company would need prior verification to open a bank account or buy real estate.
Supplier financial stability: Frequent changes to supplier information could be a red flag that the vendors can't pay their bills. Frequent data changes can also put your organization at a higher risk of making a duplicate payment.
Incomplete or invalid supplier information: Incomplete or invalid supplier information is a hot-button issue due to recent supply chain challenges. For example, suppose you are a car manufacturer and can't get critical components from China for your vehicle. If you don't have parts, you can't ship your cars to the distributors for sale, which impacts your revenue. And one of the main reasons for supply chain issues is that suppliers can't sell products because they don't have the parts. This results in a significant loss in revenue and reporting losses to Wall Street.
POs created on the day goods arrive: When a PO is created after a transaction has occurred and the vendor has submitted the invoice. This scenario indicates that your policy is not being followed or that your business lacks a formalized policy. POs created after a transaction create challenges in predicting liabilities and forecasting expenses. POs are used to expense against your budget into your forecast. When this process is not followed, it impacts your financial statements, revenue, expenses, and misstates your net income, which affects your financial disclosure.
Split POs: Splitting large orders across multiple POs to make payments above the policy limit is a red flag. Separated purchases bypass requisition and buyer controls to prevent out-of-compliance purchases and allow fraud to go undetected. For example, to get around a purchasing limit, an employee could split a PO into two transactions, each falling under the maximum amount to get around the purchasing limit policy.
Purchases with non-preferred vendors: Purchases with non-preferred vendors are commonly seen in travel expenses. For example, instead of paying a negotiated rate of $30 a day for a rental car, an employee may rent from a non-preferred vendor. You end up paying $100 per day for the vehicle, and the business experiences a loss.
Invoice processing and three-way match: A three-way match is a payment verification method used to verify a supplier’s invoice before payment. The matching process verifies the three pieces of documentation: the invoice, goods received, and purchase order to prove that the order has been filled correctly, and that payment should be made to the supplier. In your ERP system, invoices are automatically three-way matched for payment to avoid system disruptions. Minor differences between the invoice amount, the amount received from the customers, and the amount paid to the vendors are typical. Frequently, organizations have a tolerance level of 2% to 3% depending on your industry and business. Systems automatically process payments within this tolerance limit to avoid slowdowns. However, the challenge is that these tolerance limits can be changed in your ERP system on purpose, by error, reset, or disabled. This means that invoices are paid even when the tolerance is unacceptable. For example, 50% would not be an acceptable tolerance level if you only received 50% of the merchandise and paid 100% of the invoice. An ERP system will not alert management if your tolerance levels change. To be notified of changes, you need a governance system to monitor the tolerance levels, and if the parameters are changed, management is notified.
Accurate and timely payments: When invoices are not paid on time, you can incur penalties and late fees. On the other hand, making early payments can create can deplete your cash flow.
Discrepancies in freight charges: Many manufacturing companies have contracts for freight payments. For example, they have contracts detailing who will pay the freight charges, but the freight company and the supplier can invoice you for those charges, and you can end up paying double for the shipment.
Duplicate payments: Duplicate invoice payments are common and happen for various reasons. For example, a typographical error on the invoice number can trigger a second payment, or the vendor can send a second invoice with a different date. These types of errors result in cash leakage and can end up costing millions annually. For example, when we worked with a state entity, we discovered that the agency was being billed by collections and by the company that initially processed the invoice. This scenario is also common in retail when paying for advertisements. Typically you pay an agency to pay your ad bills, but the advertiser may also send a payment, and the ERP isn't able to differentiate that you are paying for the same service. The person making the payment can create or modify the vendor: Segregation of duties (SoD) is an internal control created to prevent fraud and mitigate risk. SoD ensures that at least two individuals are responsible for completing a business process. In this case, it prevents the individual from having access to create, pay, or modify a supplier. SoD breaks down processes into multiple tasks to ensure that ultimate control over a business process is never in the hands of one individual. SoD accomplishes this by splitting a transaction into two or more steps or requiring approval from another party before completion.
Can you guess what all of these examples have in common? They all highlight the need for a policy-based governance solution. A policy-based solution like SafePaaS doesn't just monitor transactions; it prevents them from occurring by governing your policies. To get an idea of how that works, let's say your payment limit is $10,000. Your ERP system will prevent the purchase of a good or service for $15,000. However, your ERP will not prevent one payment of $9,000 and another of $6000. Your ERP system will process the payments because it is not a governance solution.
To prevent the risk of split POs described above, SafePaaS will enforce your payment limit of $10,000 by accumulating the sum of the POs issued over a period of time. And if someone tries to go above that limit, SafePaaS will notify the owner of that policy or control to reject or approve that payment as a one-time exception.
SafePaaS can assess risks, design controls, and implement corrective actions on an ongoing basis. SafePaaS removes bottlenecks from your business processes and embeds your controls eliminating the risks described above.
Want to learn how SafePaaS can streamline and safeguard your P2P cycle?
Recommended Resources

MonitorPaaS™
Manual controls are ineffective without timely visibility into control violations that occur in daily business activities within enterprise applications such as Oracle EBS, Oracle ERP Cloud, SAP, and Workday. The bottom line is that if any of the key controls in your enterprise application fail to operate, there will be an impact on the business.

Detect and Prevent Profit Leakage
Organizations lose millions of dollars in their procure-to-pay processes to unintentional errors, misuse, and ineffective controls. With overpayments alone costing the typical organization a thousand dollars for every million spent, detecting problems before they escalate or even occur can drive substantial cost savings. SafePaaS Procure to Pay Advanced Controls will enable you to improve business execution via process optimization, reduce fraud and errors, and achieve compliance.

Access Governance
Control fine-grained identity access rights embedded in security roles to meet rapidly changing technology needs, compliance regulations, and cyber threats.

