Data Integrity for effective audit


Data Integrity for Effective Audit
Why audit data should be kept independent from the ERP and transactional systems
With the rapid adoption of digital transformation, more companies have transitioned to maintaining records and submitting information electronically. Regulatory oversight and intensifying scrutiny from auditors on your company's data and records management now include examining the integrity of your audit data to ensure your records' transparency, trustworthiness, and reliability.
In an audit, data integrity is of the utmost importance. However, assuring the integrity of your data is getting harder to deliver. Several factors in an audit impact the integrity of your data:
- Where your data is maintained
- How your data is managed
- Changes from your technology providers, and
- Security issues with unrestricted access to audit data
How an audit is performed
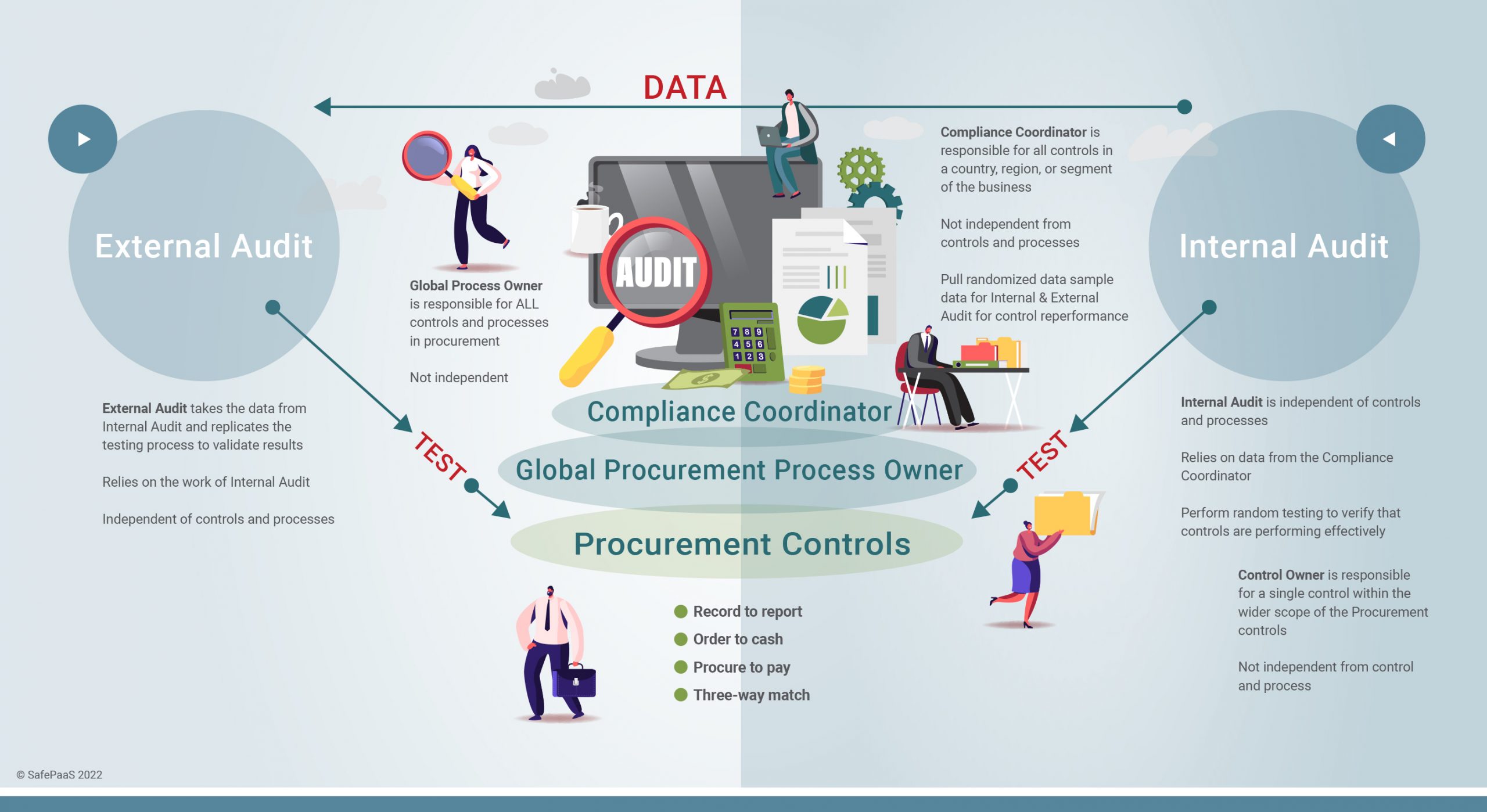
The following roles are typically involved in preparing, reviewing, and analyzing audit data:
Control Owners
Business Process Owners
Corporate Compliance Coordinators
Internal Auditors, and
External Auditors
The purpose of an audit is to review the control activities performed by the Business Process Owners (BPO) and Control Owners (CO). BPOs typically oversee the work of the COs, who have specific responsibilities to control risk within the process activities assigned to them. Once the control period has closed the BPOs pull the control data and submit it to the Compliance Coordinator.
The role of the Compliance Coordinator is to ensure the quality and completeness of the data provided by the BPOs. The Compliance Coordinator oversees the complete control function and procedures of a specific country, region, or segment. The Compliance Coordinator is part of the management and is not independent of the control process or the data. Compliance coordinators work with Internal Audit to determine what data is needed. Then the Compliance Coordinator requests the necessary data from the Business Process Owners and performs an initial assessment of the data for accuracy and completeness until they are satisfied that the data is ready to move to Internal Audit.
Once the data is deemed accurate and complete, it moves to the Internal Audit team. At this point, your Internal Audit team will work with your External Auditors to agree on the randomization of your data, and the sample size used to evaluate the internal control. This data is called control performance. Internal Audit performs random testing, observing whether the business conducts the controls effectively or ineffectively. It is common for Internal Audits to find errors because nothing is perfect. For example, your Internal Audit team may determine that the error rate of this year's data was 3% higher than last year because you received fewer products from your supplier than you expected. At this point, you can determine if this is an acceptable level of risk according to your tolerance levels.
Your External Auditors rely on the work of the business's Internal Auditors, who are independent of the company's controls and business processes. In a typical enterprise, numerous processes carry out the business's operations. With this data, the External Auditors can re-perform the control testing and repeat the control to verify that Internal Audit performed their work correctly.
The impact of digital transformation on data
In the internet age, no one physically sees POs, invoices, or any other physical control documentation. All work is performed online in hybrid environments, in the cloud. Today, you simply have data, and having accurate, reliable data becomes the control itself.
A typical enterprise has 1,000s of daily transactions happening in their business across the globe. And your IT team is tasked with extracting the data from the ERP. This requires the IT Team to write queries to pull the data. And because all your data can be extracted from the ERP as fast as a portion of your data, your External Auditors request to see ALL of your control data. However, this data has been processed and reviewed by your COs, BPOs, Compliance Coordinators, and your Internal Audit team.
Because your data has moved through so many hands, your External Auditors often have trouble trusting the reliability of your data because it is not independently sourced. Data provided by clients is considered less reliable than independently sourced data because of the ability of each party to manipulate the data. At this point in the audit, the External Auditors will ask the IT Team to share their scripts as supporting documentation. This requires the IT team to take screenshots of what scripts were run for External Auditors to rely on your data.
Challenges maintaining the integrity of your data during an audit
Data is in an open enterprise system with thousands of users.
Digital transformation has sped up the flow of data, and businesses are becoming more agile. However, we still need to control access to data to maintain its integrity. As your data passes from the Control Owner down to Internal Audit, your data is exposed at these various levels. To remain reliable, your data needs to be secured at each level. And just like your internal audit team is separate from your operations, your audit system should be disconnected from the data flow with tightly restricted access.
You can extract the data from your applications into spreadsheets and pass those spreadsheets along, but manual audits are tedious, error-prone, and time-consuming. With data flowing between six groups on spreadsheets for hundreds of controls, your data is at major risk of becoming inaccurate and incomplete, which puts your business at risk of failing the audit. An independent solution becomes necessary to ensure the timeliness and accuracy of your data.
A solution like SafePaaS removes human intervention, making your data more reliable because it's already complete. There is no need for queries or scripts, SafePaaS pulls 100% of the data with 100% accuracy. And you can control access to SafePaaS to only essential users.
Access to audit data
The integrity of your data is at risk when users who perform transactions have access to your audit system because they can manipulate the control or the data to disguise their actions. Typically, these users are part of the IT team maintaining your audit and Segregation of Duties systems. And when you put the same users in charge of both sides of the process (because you only have one IT department), it risks your data's reliability. When your data is available to users of the enterprise system, you also run the risk that those users can manipulate your audit samples. Users with access to your transactions can see the data auditors request and make changes to cover their tracks.
For example, suppose a user has access to create and pay suppliers. If your audit system resides in your ERP, then that user will also have access to see data in the audit system. And if they can see in the audit system that their fraud was detected, they could delete the control or manipulate the record to cover their tracks.
Or suppose you allow the same users that perform transactions (business process owners) to maintain the audit system. This mix of responsibilities creates an access risk. Data completeness, accuracy, and control effectiveness are unreliable because these users can manipulate the data and the control. Access to data throughout its lifecycle should be independent.
Audit data change management
Audits are not just about the current period. Audits analyze trends and variance and make comparisons to previous years. These analyses are used for reconciliations when auditors review historical data.
When auditors look at historical data, they want to compare last year versus this year. For example, if you had 5,000 purchase orders last year, and now you have 10,000 purchase orders, and that last year you had a 3% tolerance that has gone up to 6%, your auditors will want to know what's changed. The reason may be that bad suppliers are sending you bad products, or there is a security risk with a certain country changing its policies. Now you’re not getting certain materials you need to build cars in the US for example. These are the kinds of things analysis audit does. You're separately secured when you bring the data into an audit vault like SafePaaS. Your security and cloud ERP are completely independent. Unlike an enterprise system, your access is protected against security risks; data integrity is achieved through better security and governance.
To review your past year's data when fraud is discovered after it occurs, you need to be able to reconstruct the control after the fraud occurred. And you need to be able to rebuild that year's data in an independent system because only the transactions for the current cycle are in your enterprise system. After that, the previous year's data are archived. Enterprise systems can only tell you what's wrong with the data in the current cycle. But if fraud was committed years ago, you've lost the data because the previous years have closed.
Audit history is used to reconstruct a past year's audit and investigate a past event. And to do that, you need snapshots of your enterprise system. This is a unique feature of SafePaaS. SafePaaS allows you to set the snapshot intervals to create a separate audit history. With SafePaaS, your data is kept in a separate vault, enabling you to go back to any historical point. If you discover a problem, you can see what the data looked like each year and see who had access. An audit solution built on spreadsheets or bolt-on solutions can’t do that.
IT change management
Another issue facing the integrity of your data are the changes to where your ERP and Audit data coexist on the same platform. And if you are unfortunate enough to have a patch cause an issue with your data during an audit cycle, your ERP solution provider will not be able to help you. They will tell you to build a custom report to provide you with the data.
Patching can also impact your audit tool because your data and audit samples sit in the same system you're auditing. And the risk of your audit data being changed in the middle of an audit is higher.
Your enterprise cloud vendor applies changes to your system quarterly. If your vendor applies a change during your audit cycle, you will likely lose your data. To avoid this, change management should be in your IT general controls, and your transactional system should be independent of your audit system if your transactional system fails. This prevents you from losing your audit system, and you can still disclose your financial results to the market.
When your enterprise system and your audit system are independent of one another, the integrity and safety of your data are secure. Suppose you have an issue retrieving data from your transactional system; your auditor won't sign your statements. A situation like this will prevent your auditors from confirming your company's financial statements, and your stock could drop. Are you willing to risk millions of dollars of your stock price by not having an independent audit data vault?
Security problems with systems where audit and transaction data coexist
A common tool sold to companies is an application that sits within your ERP system. You can put an audit module bolt-on within your ERP where the data and security are shared. You can say that your process owners, control owners, and compliance owners are segregated. But then there's an underlying IT security risk because the IT teams maintaining all the data in the same ERP system have the access to change data.
For example, an IT person could give themselves access to create a supplier, disable the control monitor, then the audit application, and then process the payment and change it back. That IT person has changed the control because they have access to both sides by nature.
SafePaaS has modernized this whole broken process. You don't have to do anything. We create a link between our system and your system. And no human will touch the data, everything is transferred through APIs. SafePaaS receives all the data and performs a completeness and accuracy check to ensure you get 100% of the data. The system does it so that no human ever touches the data. All humans do is view the log. SafePaaS pulls all the data from your systems and eliminates the cost of labor involved in running queries and scripts, so you don't have to do anything. You're free to work on more critical projects.
Recommended Reading

Segregation of Duties and Privileged Access Policies
Eliminate false-positive filters to improve risk analysis and response. A high-performance policy engine rapidly analyzes millions of security attribute combinations and permutations across all enterprise IT systems and ERPs and business application security snapshots to report violations.

The Truth Segregation of Duties Assessment vs Management
SoD presents significant challenges for almost every company, regardless of size. Verifying SoD violations involves digging through dozens of screens in your ERP for hundreds of users to investigate potentially conflicting job responsibilities. Evaluating thousands of complex security and configuration settings through manual research on error-prone spreadsheets is inefficient. And in business, where time is money, these mistakes can easily cost your company millions.

Why review security and controls before ERP implementation
Cloud transformations are happening at incredible rates. According to Gartner, the shift to the cloud will drive $1.3 trillion in IT spending this year. Organizations are moving to the cloud with the hopes that they will reduce costs, increase agility, and improve profits. However, moving to the cloud presents challenges that must be overcome before the organization can realize the full benefits of cloud transformation, and, more often that not, security and controls are often overlooked.

