Safeguard your business with access controls that mitigate the risk of cyber threats, financial misstatements and fraud in Oracle Applications

Streamline user security management process with workflows
that prevent security risks from user access requests
Use audit analytics to detect segregation of duty violations, data breaches, fraud and other security risks.
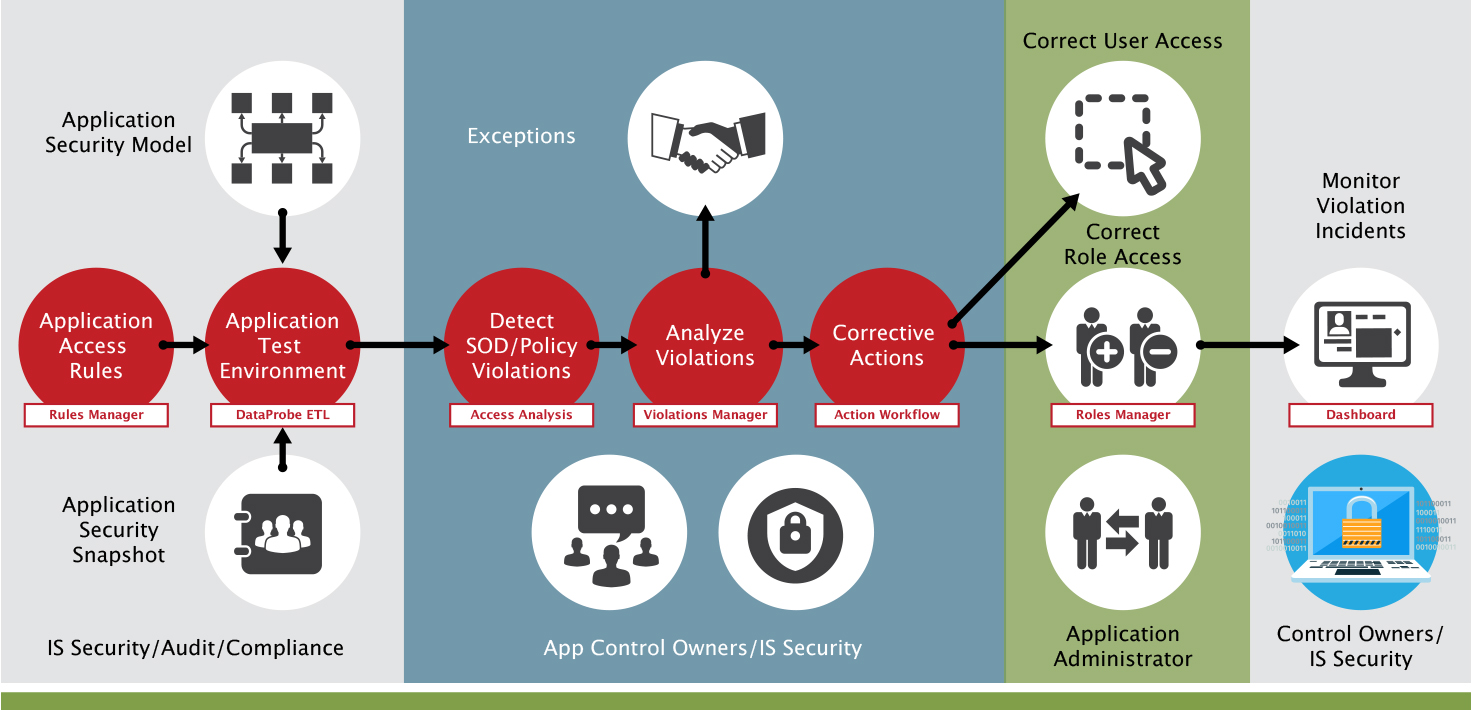
The standard user security administration tools available within enterprise applications are not sufficient to mitigate the growing risk of fraud, financial misstatements and operational losses. Business Managers, Application Security Administrators and auditors can’t rely on the standard user responsibilities assignment process where users are granted access without necessary policy checks and approvals.
You can automate and streamline the application access controls management process by detecting user access risks in the existing ERP security model where the users have access to sensitive or conflicting functions. Access risk can be mitigated by re-configuring the application roles that contain inherent access risk. In addition, you can reassign roles where combined entitlements across all the roles, assigned to a user, are in compliance with your company’s access policies.
After remediation of access risks, it’s important to prevent any future access policy violations by establishing an access request workflow where all new access requests are analysed for policy violations and approvers can make decisions based on the access risks before a user is granted access to new application privileges.
Read the rest of the article for best practices to remediate access risks, implement Segregation of Duties and prevent recurrence in the future. However, we must recognize that most organisations have to tolerate some level of access risk where the business resources are constrained. For example, in a small remote business unit, you may have the same person enter and post journal entries. In such cases, you can deploy Continuous Controls Monitoring (CCM) to identify suspicious transactions, alert process owners when key application configurations are changed by “super users” and maintain audit trail over data changes such as customer credit limits, supplier bank accounts etc. CCM should be considered as part of your compensating control strategy to manage overall access risks.

