Enterprise Access Certification Manager
Automate User Access Review and Certification to control access across all Cloud and on-Premise business applications.

Streamline the access review process with automated workflows
Reduce the cost of SOX compliance and mitigate cybersecurity risks.
Quickly and reliably limit access to sensitive privileges and data to only authorized users.
Ensure sensitive data is kept safe from malicious actors.
Reduce cost of SOX compliance.
Mitigate cyber security risks.
Manage and control access to meet audit standards
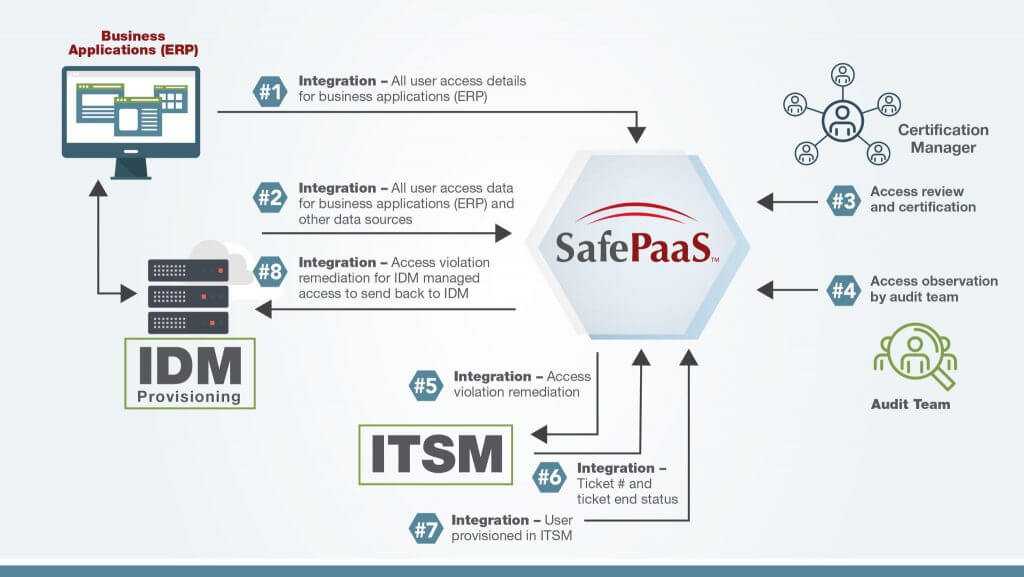
Prevent the risk of application access control failure by completely automating the enterprise certification process for ALL IDENTITIES across the application and ALL other data sources, including IDM, IGA, ITSM, Database, and Servers.
User access is a common source of internal abuse and a principal focus for IT Audits. It’s critical for organizations to know who has access to their systems and what they are doing in those systems. The enterprise application landscape coupled with data flowing in from multiple sources are huge challenges for organizations to manage .
Rising cyber risks, insider threats, and growing scrutiny from auditors are increasing the demand for organizations to streamline and automate the user access certification process. Not only are auditors increasing their demand for a streamlined user access certification process, but they are also demanding complete, accurate and timely user access certification because it is a key control for financial risk and compliance management.
Rapidly growing cybersecurity risks have further increased the need for businesses to follow the National Institute of Standards and Technology (NIST) Cybersecurity Framework. The NIST framework provides risk response guidelines to threats businesses may face. Cybersecurity measures include access review to limit access to sensitive privileges and data to only authorized users. Any unauthorized access must be terminated to eliminate any threats. Without effective access controls, businesses cannot ensure the sensitive data they are responsible for is kept safe from hackers and cybercriminals.
In today’s face-paced hybrid work environment, it’s critical to have complete confidence that the access and privileges granted to users are limited to their job role and only to the necessary applications. Access and privileges should also be periodically verified by management.
SafePaaS Enterprise Certification Manager™ makes it easy to manage and control access to meet the audit standards established and expected by major audit firms. Automating the certification process replaces a manual time-consuming task, often done via email and spreadsheets, but also ensures timely, complete and accurate results ensuring compliance. Automating access review saves organizations hundreds of hours each quarter, that requires management to review access of role assignments and privileges within business-critical applications.
Features
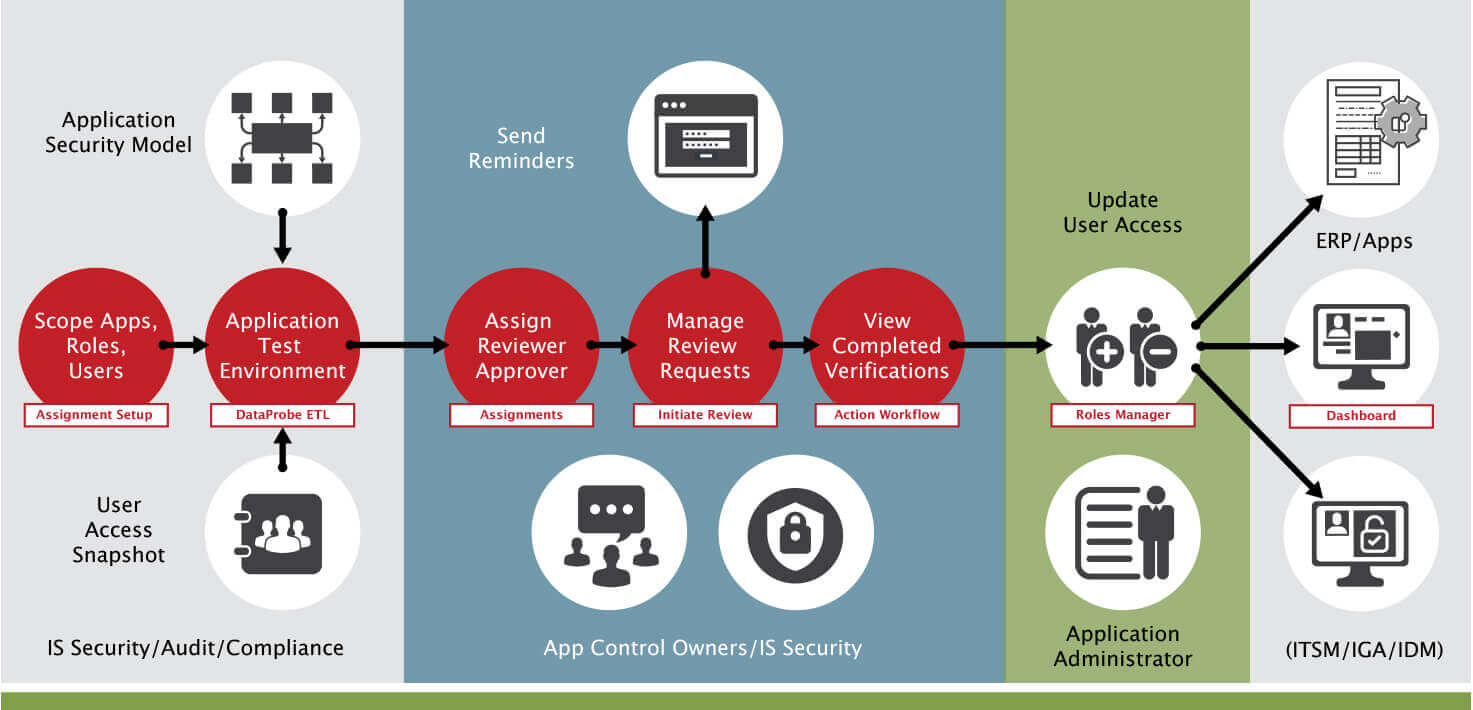
Certification Managers can efficiently complete periodic certification surveys by accessing a deep link to the certification page. Here certification managers can see all user-role access records assigned to the certifier. Users can start the certification using the Single-Sign-On (SSO) ID already given to them or receive a one-time Passkey to certify the users’ roles. User information is augmented with role usage frequency and provisioning records from business applications and ITSM systems to ensure that certifiers can perform this key control activity accurately.
Certification Administrators can set up, initiate, and monitor certifications for all business applications, databases, servers, and other data stores using a consolidated controls panel. Administrators can set up the survey by cross-linking user security information from multiple sources such as business applications, IT Services Management, Identity Management, and Access Request Provisioning systems. The survey can be initiated using filters to ensure compliance with policies while preventing time-consuming, redundant activities. These filters include application environments, access risk levels, access groups, etc. Analytics are available to monitor progress using dashboards, track completion status, send reminders to certifiers, and prepare audit reports.
Once the certification survey is completed, any access change requests to remove one or more role assignments for a user, expressed by the Certification Manager, are issued and monitored for timely risk remediation within SafePaaS and any integrated IT Service Management Systems such as ServiceNow.
Enterprise IT leaders and service delivery managers responsible for access controls can lower IT cost of ownership by eliminating manual activities. Activities that are frequently required to execute corrective actions after each certification. User access change requests can be synchronized with ITSM and IGA systems using self-service integration services on the platform.
Intelligent Survey Initiation options can reduce the audit burden on management by eliminating redundant requests where the risk is lower than the threshold and accepted by management for user roles such as “birth-rights”, fire-fighters, service accounts, and robotic process automation (RPA).
.
Certification Survey displays the fine-grained entitlement details to prevent common sources of ITGC control failure where the provisioned roles are only abstracted at the job level – as often is the practice in configuring a roles catalog in ITSM, IDM and IGA systems. The lack of accurate representation of user privileges within entitlements granted by roles can result in a control failure where the privileges granted in the business applications are elevated due to security configuration changes e.g. “Payable Inquiry” role that allows the application user to create a supplier, or approve payments.
.
Whether your identity access certification includes applications in the cloud or on-premise, you can rapidly deploy certifications by choosing from a wide range of industry-standard protocols for integration. These standards include JDBC, REST and SOAP and formats including CSV, XML and JSON allowing you an easy, quick, and secure way of scoping the applications and data sources for the certification.
Learn how a global household brand ensures reliable access certification across the enterprise